

|
Sam's Cryptocurrency Service© |
|---|
|
Sam's Cryptocurrency Service
Introduction What Are Cryptocurrencies? Searching the internet, we found the following definitions: Cryptocurrency is a form of currency that exists only in digital form. Cryptocurrency can be used to purchase online without going through a mediator, such as a bank, or it can be held as an investment. Buying cryptocurrency doesn't grant you ownership over anything except the token itself. It is more like exchanging one form of currency for another. If the crypto loses its value, you would not receive anything for it. Structuring and Securing Cryptocurrency: We are rewriting this page with the hope of not being too technical for our nontechnical audience. The Goal: Our Goal is to make Cryptocurrency services as good as the banking services if not better. We need to set up some basic understanding of what we mean by Structuring and Security Cryptocurrency as a Business. What does it mean to structure a business? We believe that structuring a business is planning, organizing, configuring and building the foundation for the business to run and grow. The foundation or the infrastructure is the base that business is built on. Such business foundation needs constant monitoring and maintenance. What does it mean to secure a business? When it comes to securing Cryptocurrency, we need to address a number of issues starting with Cryptocurrency monetary value, transactions, Cybersecurity, banking, exchange, investment, ..etc. Cryptocurrency is a digital currency and when it comes to the monetary value of a currency, we need to look at USA Dollar. With US Dollars, anyone can go to any country and would be able to use US Dollars to pay for goods and services, exchange or even deposit in banks. The US Dollars are backed up by US Government and US business finance. Therefore, our security goal is to build a monetary system compatible to the US Dollar. Our Target Audience or Clients: • Cryptocurrency Companies • Cryptocurrency Plateforms • Cryptocurrency Dealers • Cryptocurrency Exchange • Cryptocurrency Broker • Banks • Investors This page presents: 1.0 Cryptocurrency Foundation or Structure 1.1 Cryptocurrency Federation - Governing Body 1.2 Business Unit Federation of Cryptocurrency 1.3 The Federation of Cryptocurrency Companies 1.4 Cryptocurrency-Coin Clusters of Companies 1.5 Structuring and Tracking Cryptocurrency (Holder - Coin) 2.0 Our Service - What are we selling? - Our architects and tools 2.1 Securing Cryptocurrency Transactions 2.2 Using Virtualization 2.3 Proxy and Rerouting Servers and Distributed Cloud Plus Alerts 2.4 Our Vertical and Horizontal Security Architect 2.5 Integrating our Structure and Tools into any Existing System 2.6 Virtual Testing 2.7 Building Machine Learning Tools as Background Support 3.0 Security 3.1 Securing Cryptocurrency as Buisness 3.2 Securing Cryptocurrency Processing 3.2 Securing Cryptocurrency Future 3.4 Securing Cryptocurrency Growth 4.0 Transactions 4.1 Cryptocurrency Services 4.2 Cryptocurrency Transactions 4.3 Cryptocurrency Banks 4.4 Cryptocurrency Exchange 5.0 Models 5.1 Computer Models 5.2 Virtual Testing of Computer Models 6.0 Implementation 6.1 Cryptocurrency City 6.2 Cryptocurrency Business Unit 6.3 Cryptocurrency Franchise 1.0 Cryptocurrency Foundation or Structure According to Tanya Zhang, co-founder of Nimble Made: "Cryptocurrency is currently all the rage, but keep in mind that it is still in its infancy," "Investing in something new comes with its own set of obstacles, so be ready. If you want to participate, do your research beforehand and start with a small investment." We need to learn from history and the existing system. Therefore, how to build the foundation may require quite a bit of research and hard decisions. For example, there are different types of company such as stock companies, mutual companies or individually owned. We are open to different types of foundation. 1.1 Cryptocurrency Federation - Governing Body Searching the internet for "What are governing bodies in government?": A governing body is a group of people that has the authority to exercise governance over an organization or political entity. The most formal is a government, a body whose sole responsibility and authority is to make binding decisions in a taken geopolitical system (such as a state) by establishing laws. We recommend that there is should be a Cryptocurrency Federation with a governing body and free from any government. The governing body would creating the bylaws. What are governance bylaws? Bylaws are the legally binding rules that determine how an organization is to be operated and also how the organization's board will operate. Bylaws are a guide and reference on how a club is structured, what rights the members have, and the procedures by which those rights can be put into effect. 1.2 Business Unit Federation of Cryptocurrency Introduction: What we are presenting a very simple and powerful concept and a tool to help a Business Unit such as US Steel and Auto-manufacturing companies. Examples of these companies are the steel manufacturing companies, big auto manufacturers and trickledown to small shops making screws and bolts for almost all the auto business as a whole. These companies must borrow from banks or sell stocks to create the needed revenues to start new projects or maintain processing in case of bad economic year or any tough year. The biggest part of the concept is the money needed by every company in the Business Unit to function. The needed capital given by the banks is nothing but an Electronic Credit. Due to the COVID-19, the US government borrowed $7.7 trillion and the only thing the US government got is also an Electronic Credit for US government to use to function. Therefore, if our Cryptocurrency Federation can replace the banks' Electronic Credit with their won Electronic Crypto-Credit, then the Business Unit as a whole would no longer need banks, and would be free from banks and their interests. The Business Unit would function independently without worrying about banks, interest, bad economy, federal regulation or anything outside the Business Unit. In short, the Business Unit would be a country within a country. We also like to add that the details of building such Federation for the Business Unit is not simple. With the assumption that we have a perfect world, then US Steel and Auto-manufacturing companies Business Unit would not need any form of outside finance and selling their products to the outside world is the incoming flood of capital. All they need is to buy the row material, pay their utilities and employees and all their internal financial transaction would be done using the Business Unit Cryptocurrency. Using Computer Models and Virtual Testing: Computer Models and Virtual Testing are nothing more than tools which are used to build things more efficiently, economically, eliminate errors and costly mistakes. It also speeds up the execution of building things. Actually, such tools can be the decisive factor between a project that is doable or out of reach. Hollywood and moviemakers use "Computer Models and Virtual Testing" to make-believe of things such as the futuristic existence of galaxies, plants, buildings, war equipments and spaceships as shown in the "Star Wars" movies. So our job as analysts is to simplify "Computer Models and Virtual Testing" so the common man would understand and see the benefits of such tools. Sam's Interest Free Town (Cryptocurrency City): Using Computer Model, we can create a self-sufficient small town with 1,500 residents. The town's structure is city government, main bank, small number of businesses which employ the town's population, schools, a number of farming business which supply the town with all food and a number of stores. The main bank provides all the financial support for such a town to work and live. Nothing comes in, nor leave the town. All transactions are done by borrowing from the main bank and then pay back what is borrowed plus interest. If the town's residents decided to use Cryptocurrency and stop borrowing from the bank, such a town would survive and it would save the main bank's charges, interest and dependencies on the main bank. New projects and any new improvement would not be tied by the bank's decision to finance or refuse the funding. Cryptocurrency would replace the bank and its services. It would also eliminate theft and corruptions since every resident would be part of the finance. Cryptocurrency would be limited and it can only be used within the town. We would be creating two models of Sam's town, the first with the main bank as the town's finance and calculate the pros and cons. The second model would be using Cryptocurrency as the town's finance and calculate the pros and cons. Such computer models and virtual testing (virtual means only exists in computer memory), we would have a true picture of how Cryptocurrency can help us. Computer Model and Virtual testing would also give a true picture of what we need to make our life better and plan for our future. Note: There is no limit on the number of models we can create to see all the possible scenarios. There will not be any hurdles for the town's growth, nor will stop the business healthy competition. Cryptocurrency would give opportunities for individual's growth, and increase the personal finance and status. 1.3 The Federation of Cryptocurrency Companies: To give the business of Cryptocurrency credential and credibility, the business of Cryptocurrency must have a solid structure and members whom they would protect its structure. The main role of any government is protection and in the absence of a government, there must be a governing body that provides the protection. We recommend that a number of Cryptocurrency Federations. The following are some of our Federation types and we are open for brainstorming our structure and approach. • Public Sector Federation of Cryptocurrency • Business Unit Federation of Cryptocurrency Public Sector Federation of Cryptocurrency Any company issues Cryptocurrency coin for the public must be a part of a Federation or League where they would be certified and bonded plus published in The Federation of Cryptocurrency Companies. This would eliminate fraud plus each of The Federation of Cryptocurrency members would have to pay a bond against the number of coins they would be issuing. No government should be part of The Federation and only private sector would be the governing body. The Main Issue - Service: Cryptocurrency as a business suffers from a number of serious issues and the center of all these issues and the future of Cryptocurrency is Service. Service may have different meaning or value for different participants. For example, personally:
The answer is Service. For example, banking is nothing but a service that we trust despite fact that all banks' customers know that these banks are taking advantage of us and our money (the reason for Cryptocurrency revolution). Service has to use technology and be conveniently, available 24X7 using our PCs, mobiles or other electronic devices. Cash transactions is still critical to almost all of us despite most of the world dealings are done electronically. Securing Cryptocurrency services and make them electronically convenient are the basis for building the Cryptocurrency as a financial business. Tradition of the Banking Services: Banking traditional thinking is you deposit your money (fund) into your choice of a bank to store your fund. Direct deposit is another option. Your bank would provide personal services suhc as depositing, cashing, buying, trading, paying for purchases, ..etc plus you are free to access your funds. Banks are credited institutions and not a con or a fraud. 1.4 Cryptocurrency-Coin Clusters of Companies Cryptocurrency is in its infancy and we need to protect all participants and specially Coins companies. We proposing that there should clusters of Coin companies which would help prevent hustle takeover of small cryptocurrency Coin companies. We are open to work with any cryptocurrency Coin company and plan how to protect all participants. 1.5 Structuring and Tracking Cryptocurrency (Holder - Coin): We are presenting a structure to the Cryptocurrency as a finance vehicle for people to save, make payment and invest the same way as US Dollar, any currency or stocks. We can learn from how money and stocks are used, but we are trying to simplified as much as possible. We simplified Cryptocurrency structure to secure and track any transaction with dynamic and robust structure. Our attempt is to minimize confusion and reduce the risk of losing coins due to hacking, theft or losing IDs. Our structure would help in speeding, securing and tracking any coin and its holder and their transactions. We are borrowing some of existing financial options such as saving, trading, cashing, borrowing, payment and treat coins the same way we treat properties including liens, finance and refinance transactions. The Basic structure is as follows: • Holder • Coin Holder: A Holder can be a person, a couple, a group of people, a company, a government, a bank, or a Ghost. A holder owns one or more coin. The Holder has identifications options: • ID Only - Ghost Account • Personal ID - Personal Account ID Only - Ghost Account: An ID only - Ghost Account is where a holder has only an ID. There is no other information about the Holder and that has the risk of losing ownership if the ID is lost. The Holder can add other data as part of the ID structure-record if the holder wishes to keep his/her privacy and being anonymous. For example, a Holder can be a Ghost with a structured number (Time of purchase, ..) to identify that that Ghost owns one or more coins. The Ghost can add other data as an additional help to prove that a coin does belong to the Ghost. Personal ID Data: Personal ID is similar to any bank or stocks information. We would be adding few security, audit trail and tracking parameters. Coin: We categorizing coins' values as Gold, Silver, Dollar or any category which distinguish the coin value. A Coin is nothing but a virtual coin which a Cryptocurrency company (let us call it Company CRPTO_XYA) would issue. CRPTO_XYA is the one who is holding the value (dollars, gold, silver, ..etc) of CRPTO_XYA coins. Therefore, CRPTO_XYA would be able to sell Dollar value coins, Gold value coins or Silver value coins or other value options. Coins would be company specific. For example, I can buy a Silver coin from CRPTO_XYA and CRPTO_XYA would hold the value of such a coin. CRPTO_XYA can also offer dividends or interest on its coins as an incentive for people to buy from CRPTO_XYA or invest. Different Cryptocurrency companies do not share the same Coin. Coin Types: 1. Personal Coin 2. Trading Coin 3. Cash Coin Personal Coin: A Personal Coin would be similar to saving accounts (with possible accumulating interest or dividends), where the owner of the account can cash the coin value or borrow against it. Each coin has only one owner and the coin is not transferable. Personal Coins would eliminate the risk of being stolen, hacked or destroyed. In short, Coins are safe in the Cryptocurrency saving account. If the Holder cash the coin, then coin is totally destroyed and only the coin's audit trail would exist. Personal Coin - Lien Option: Personal Coin can also have a lien option to help with easing financial transaction. Cryptocurrency Dealers, Cryptocurrency Exchanges, Cryptocurrency Brokers and Banks can put a lien on a Personal Coin if the Coin Owner has some kind of financial transactions with them. The lien flows the same liens rules on properties. Trading Coin: Trading Coin as the name implies, the Coin Holder has the option of trading the coin. Each Coin comes with its own unique ID as an another added tracking of ownership. The Ownership of the Trading Coin is transferrable. Each Trading Coin has an audit trail or history of ownership. Even if a Ghost owns such a coin, we would be able to track the coin to the Ghost ID plus other ID data. Cash Coin: Cash Coins are Used for quick payment to any institutions or shops which accept coin payment. It is more like writing a check or debit card. Coin and Holder ID Numbers: We need to brainstorm these IDs and we have structure for IDs. Holders of Trading Coin Credit Score: Holders of Trading Coin would must pass some credit score based on the number of error free trades to reduce fraud. For example, A Holder of Trading Coin can 10 of 10 trading scare which all the Holder's trades were perfect without any issues. The Trading Coin audit trail would have such credit score and updated as The Holder does more the trade. Cryptocurrency Companies may refuse to sell coins to Holder with bad scare. Cryptocurrency Companies may cash out Coin Holders and band any transaction with such bad scare Holder. All the data about the Holders on the Coins would encrypted and compressed for security and the Cryptocurrency company issuing the coin would be responsible for all these data. 2.0 Our Service - What are we selling? - Our architects and tools With over 25 years developing system and being pioneers in many evolving technologies and platforms, we see Cryptocurrency as a new challenge and again deja vu, we have been there and done that. We are selling the know-how plus the seed platform to build an enterprise cloud umbrella from End-2-End including structure, security, tools, development, DevOps, DataOps, Machine Learning and technical lead and management. This webpage is a quick presentation to answer anyone interested in Cryptocurrency starting with investors and Cryptocurrency-Coin enterprises. 2.1 Securing Cryptocurrency transactions Again, when it comes to securing Cryptocurrency, we need to address a number of issues starting with Cryptocurrency monetary value, transactions, Cybersecurity, banking, exchange, investment, ..etc. We are focusing on Cybersecurity, Computer Models, Virtual Testing and Machine Leaning. Spreading Services and User Interface - Store, Branch and Trading Post: Issues: One of the biggest issue is the number and sizes of hackers' attacks. We cannot stop such attacks but we can force hackers to perform a lot more work and specially if they are using Machine Learning in their relentless attacks. The following are some of possible hackers attacks:
Our Recommendation - More Targets: We recommend that Cryptocurrency websites would be categorized as follows: • Type of Coins = Gold, Silver, Bronze and Dollar, other options • Type of Transactions = Store (buy and sell), Branch (transactions), Trading Post (trade and exchange), or other options Cryptocurrency Companies websites could be a combination of these options: 1. Gold Store 2. Gold Branch 3. Gold Trading Post 4. Silver Store 5. Silver Branch 6. Silver Trading Post 7. ... The development of these websites would use virtual servers and virtual IP addresses to be able to handle any attach and divert traffic and warren their clients. The clients or websites visitors may have issues with such a number of options to choose, but they need to remember that we scan our shoes in every airport. Now the hackers need to put more effort with every attack. We also recommend Cryptocurrency Companies websites and their brokers websites would be responsible in keeping their clients or custmoers' data. We recommend that they would have more than one websites with a separate independent system where these website would responsible for different transactions. We recommend a distributed cloud with GoldenGate backup system. Websites Graphic and Contents: Each website graphic and contents should look different and maybe a color code and visitor ID would be shown in the ID section of the website which the Cryptocurrency clients would recognize. Our attempt is to make mimicking or copying websites a lot more challenging specially with color code and IDs. We recommend that each site would have its own independent system spread the transactions for hackers to handle since each site would have its own security parameters for hackers to attack. Encrypted ID and Device IDs: Using Mobile Text, Memory Sick, Phone/PC Device as an ID number. These ID would encrypted plus these encrypted IDs would be indices for hashing the issued ID for the Holders and Coins. Therefore, if the hackers get a hold of any ID, that would not help them since the ID is nothing but an Index for one of the Hashing Tables with real values. The system internal structure would be secured. 2.2 Using Virtualization: This is too big to cover at this point plus based on the system architect and cloud services virtualization would be components dependent. 2.3 Proxy and Rerouting Servers and Distributed Cloud Plus Alerts: Proxy Servers: Proxy servers would be the front buffer in case of hackers attacks and would be designed to identify the types of attack and start filtering and rerouting traffic plus start sending alerts to clients and visitors. Proxy and Incoming Traffic Filtering: Our Proxy servers and firewalls would be able to filter the incoming traffic and counteract any DDoS attacks plus other attacks. Alert System: An Alert System would handle communication with clients to use different IP addresses and look out for issues or problems. Encrypting Data: Users' data would be encrypted and would not be of any value to Man-In-The-Middle Attack (MiTM) attacks. Rerouting Servers: Using virtualization to create new virtual servers or system with new IP address to stop further attacks. Distributed Cloud: Our Distributed Cloud would have the capabilities to handle any hackers attack. How such capabilities is created, we would provide a number architects based on the clients resources. 2.4 Our Vertical and Horizontal Security Architect: Security is the center of building Cryptocurrency services and we are proposing our security approach with our Vertical and Horizontal Security Architect. Vertical and Horizontal Scaling Definitions: • Vertical means each Unit is modified to have more power, functionality, production, flexibility, .. etc. • Horizontal means add more units. 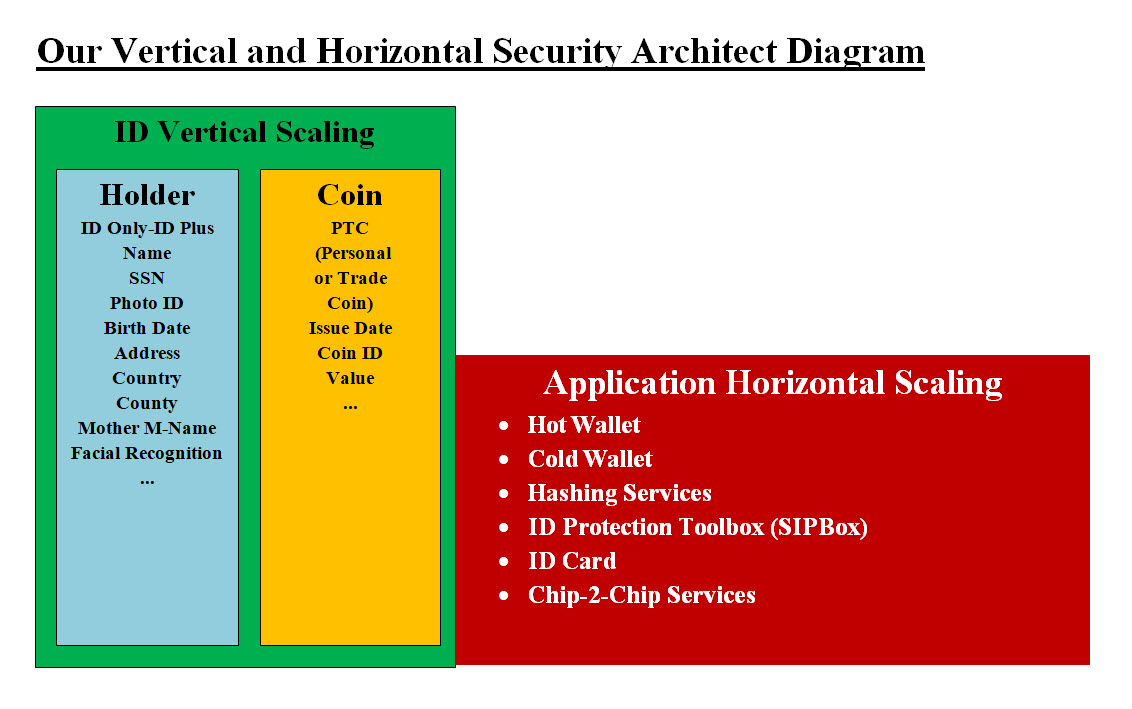
Image #1 Image #1 is our Vertical and Horizontal Security Architect Diagram with our system's Vertical and Horizontal components. ID Vertical Scaling: We are architecting our Vertical Scaling as the ID components of our system security. It is composed of the Coin Holder and the Coin itself. Each has a unique ID to help with identifying the Coin Holder. Application Horizontal Scaling: Application Horizontal Scaling is which application our clients would be using. The clients may choose their existing Hot or Cold Wallets or use our architected applications. We add the following applications to the Hot and Cold Wallets: • Hashing Services • ID Protection Toolbox (SIPBox) • ID Card • Chip-2-Chip Services Chip-2-Chip Services: Our Chip-2-Chip Services is our Encryption-Compression Chip. Our Chip can be used by PCs, mobile, tablets or any cloud system. Before we get to be too technical and get our non-technical audience lost. Let us look at the following example. Let us say that your PC has our chip and you need to perform a Cryptocurrency transaction (buying, selling trading, ..etc), and you want to logon our site Sam_Cryptocurrency.com. What you have as security parameters are: 1. PC device ID 2. Chip ID 3. Your Login Name 4. Your Password Your internet connection (request) to Sam_Cryptocurrency.com would be done by our chip and our chip would sent your PC's ID, Chip ID and current time (timestamp) plus a number of security parameters. Sam_Cryptocurrency.com would return (reply) with an entire separate system (virtual server with its own operation system, transaction application and keyboard buffer) compressed-encrypted. The reply system will run on your PC as if it owns and block anything from running. Please note that our chip would verify income code and start decompressing-decrypted the income system and runs it. Our chip on your PC would be the only one which communicate with Sam_Cryptocurrency.com, decompressing-decrypted plus check a number of security parameters. Now you have a newly (virtual) system which would perform all your secured transactions. The new system would ask you for login name and password and start your transaction. The chip and the new system would be communication with Sam_Cryptocurrency.com to perform the updates. The newly installed system can be used to save data on memory sticks as well as print. Once your are done then the entire newly installed system would be wiped clean from your PC. You also would have saved your transactions on your memory stick and printed as you would wish. Our Chip has the power to compress-decompress the size of the newly reply system to 20% of its size (saving over 80%) and encrypted-decrypted with speed of your PC's CPU. This translates into fast and small size of bytes in both request-reply and hardly any performance issues. The virtual system running on your PC would like any bank application with all the Cryptocurrency functions. The same is done with tablets. As for mobile, our chip would install a new App and removed totally from your mobile device as well as not share or perform any image processes. As for chip being stolen or used by someone else we would answer that in the next sections plus your device has its own unique personalized chip. For example, if the same file (compressed system) is received by your PC, tablet, phone or any device, only one would be able to decompress-decrypt the file and no other device. The other chips used by other devices would not be able to decompress-decrypt such a file. Hashing Services: What does the term hashing mean? Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string. The most popular use for hashing is the implementation of hash tables. Hashing is one way. It's technically possible to reverse-hash something. Encryption: To encrypt data you use something called a cipher, which is an algorithm, a series of well-defined steps that can be followed procedurally. Encryption is a two-way function, to encrypt and decrypt information. Number Game: An illegal lottery based on the occurrence of unpredictable numbers in the results of races. Packets: The internet is highways of data traveling from one computer network to another computer network. Data is packaged in small amounts of data known as Packets. Our Hashing: Hashing can be used to mask or hide values. When it comes to Cybersecurity, hackers with the help of reverse engineering, Machine Learning, Man-In-The-Middle Attack (MiTM) and speed of computer can figure out the hashing values or how it is implemented. To make hashing a bit more difficult to figure may required some sort of combination of hashing Encryption. Also adding dynamic values such system clock to hashing-encryption would make a bit more difficult to figure even if you have the code. This known as Number-Game. Our Cryptocurrency Security implements Hashing by using indices to tables and the tables contents would be used to figure or find the ID number or values. Therefore, there is a two layers of Hashing-Encryption. Clients can send values or numners from their system or mobile and the following numbers would be encrypted before they are send in the data Packets: 1. Using Mobile Text 2. Memory Stick 3. Phone/PC Device ID or number as an ID number 4. User ID 5. Date of Birth 6. Home Address number 7. System clock 8. Misc number based on security parameters Note: Hackers may have access to some of these data, therefore our Hashing-Encryption would implement the Number Game. By the using the system clock and encrypting it would be also be tough to figure out. Well Documented and Tested Hashing-Encrypted Code: All the Hashing-Encrypted code must be well documented and tested before it moved to production. ID Protection Toolbox (SIPBox): Our ID Protection Toolbox (SIPBox) is a part of our Object Oriented Cybersecurity Detection Architecture (OOCDA) Suite and the following link is the page: http://sameldin.com/OOCDProjectSite/ID_ProtectionToolboxPage.html ID Card - Coming soon A mobile Credit Card Reader: A mobile credit card reader is a device that you attach to your Smartphone so that your phone can act as a credit card reader. These devices enable payment through traditional credit card swipes, chip payments or contactless payments. We are working on implementing a mobile credit card reader and we are still in the research stage. No more Wallets Virtual Testing The cost and return on the investment FAQ Coming soon 2.5 Integrating our structure and tools into any existing system 2.6 Virtual Testing 2.7 Building Machine Learning tools as background support 3.0 Security 3.1 Securing Cryptocurrency as Buisness 3.2 Securing Cryptocurrency Processing 3.2 Securing Cryptocurrency Future 3.4 Securing Cryptocurrency Growth 4.0 Transactions 4.1 Cryptocurrency Services 4.2 Cryptocurrency Transactions 4.3 Cryptocurrency Banks 4.4 Cryptocurrency Exchange 5.0 Models 5.1 Computer Models 5.2 Virtual Testing of Computer Models 6.0 Implementation 6.1 Cryptocurrency City 6.2 Cryptocurrency Business Unit 6.3 Cryptocurrency Franchise |
|---|