
Sam Eldin |
CV - Resume | Tools 4 Sharing | Architects 2 Show | Big Data Presentation | Android Training | Java-Unix Code Templates | Interviews QA & Code |
|---|
|
|---|
|
Security Solution Architect - Adam's Blueprint for Security
This page is called "Adam's Blueprint for Security" so we would answer as well as give credit to a friend of us named "Adam". As we were discussing with Adam our approaches, architects and design, his reply was: "Do not sell me fish in the Ocean, give me a blueprint" His first question was: What would you do when your network is attacked? This page's content would cover Adam question, our Blueprint plus a quick introduction to Cybersecurity with images. We also like to add that anytime we start presenting our automation, virtualization, intelligent and security, sadly most people would get defense and they would be reluctant to admit that they do not understand and they would keep quiet. They also may drop the subject all together. We would answer Adam's first question and then start with quick introduction for both technical and none-technical audience. Adam's first question was: what would you do when your network is attacked? Our answer is: it must be done by man and machine with the following processes: 1. Detection 2. Vulnerability Assessment 3. Risk and Risks Handling 4. Fixing the Issues 5. Testing Our Main Topics for This Page: • Introduction • Automation • Intelligence • Virtualization • Blueprint • Adam's Question Revisited Introduction: It is critical that we present in Image #1 a rough image of cloud, software, hardware, internal hackers, security layers and external attacks. Images #2 is what we call analysis of hackers attacks and the relationship of attacks and networks tiers. Sadly, hackers have the upper hand since system are sitting docks for target practice. Not to mention there plenty of items to attack at anytime or at attackers convenience. Coordination of attacks with the support of Artificial Intelligence are growing, getting more sophisticated and have devastating damages and lose of revenues. 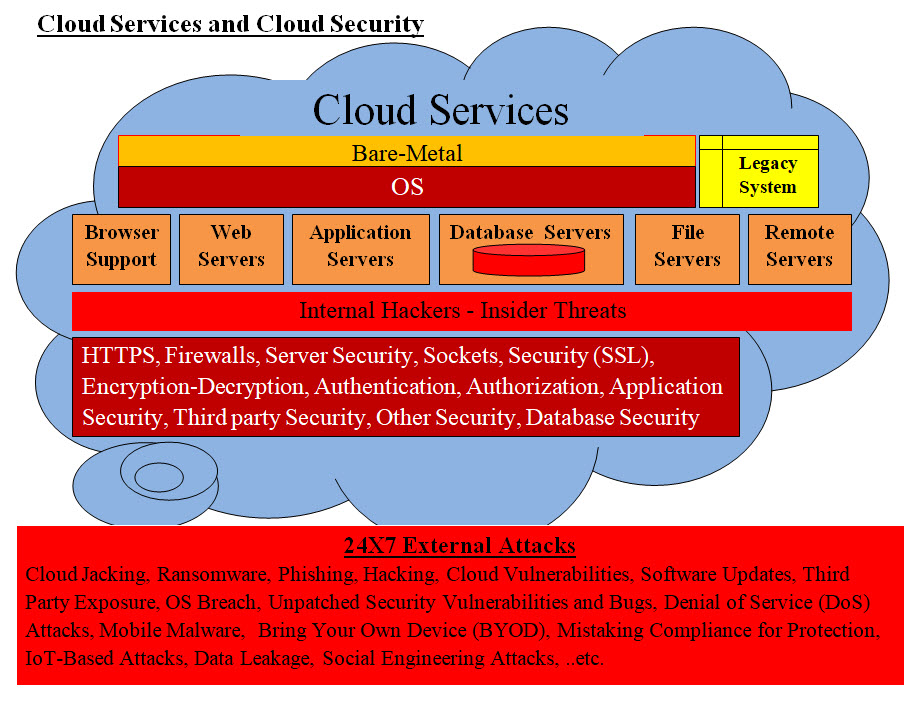
Image #1 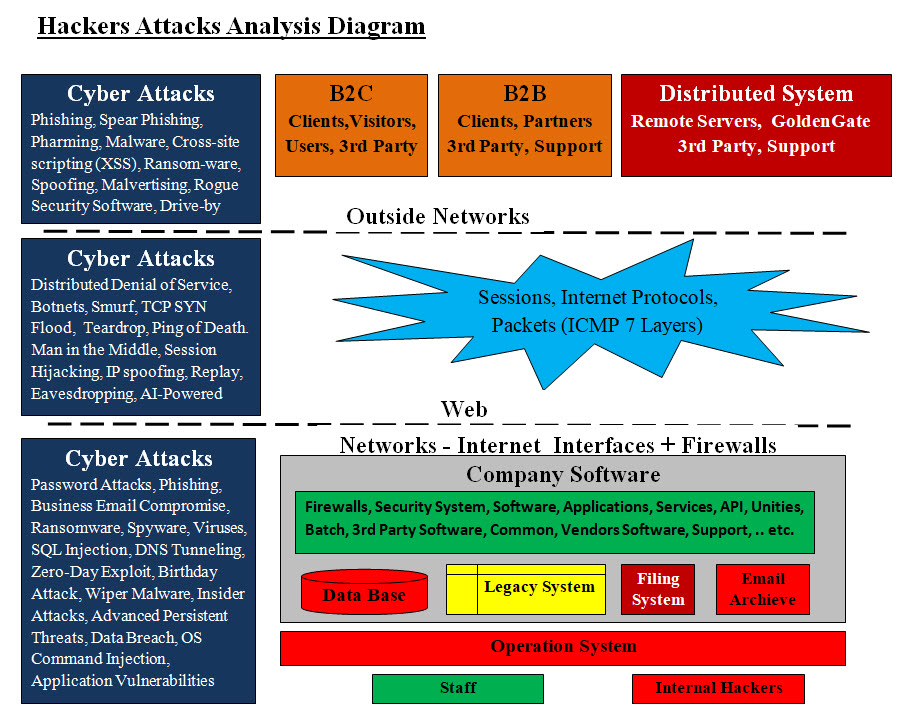
Image #2 Looking at Image #2, anyone can see that hackers did not leave any room without lunching multiple level and types of attacks. Zero-Day Attack, Reverse-Engineer of Patch Code and Internal Hackers are the toughest challenges which Cybersecurity must deal with. Automation: Our view of automation is building roadmaps of processes and steps. These roadmaps can be used by human with their intelligence and machine with their astonishing speed and great number of possible options. Such speeds and options would be used to add intelligence. First, looking at any network, there are hundreds of thousands of items running on any giving network (software and hardware). To handle hundreds of thousands of items, automation is must ant not an option. Tracking or testing these items is a challenge. Our approach is "Divide and Conquer". Therefore, we need start with one target network or small network and divide it into logical and physical units. We build what we call Matrices of processes or steps. For example, the following matrix in Images #3 would be used by human and machine to perform a number of tests or tasks. Any task or a test should be a small script which runs by human and/or machine. Such script should return a value to the caller for tracking and feedback. The script starting and the ending time is critical in evaluating performance. Not Applicable (N.A.) would be used so we can build big matrices with Nemours items. Some tests may not be applicable by some items. 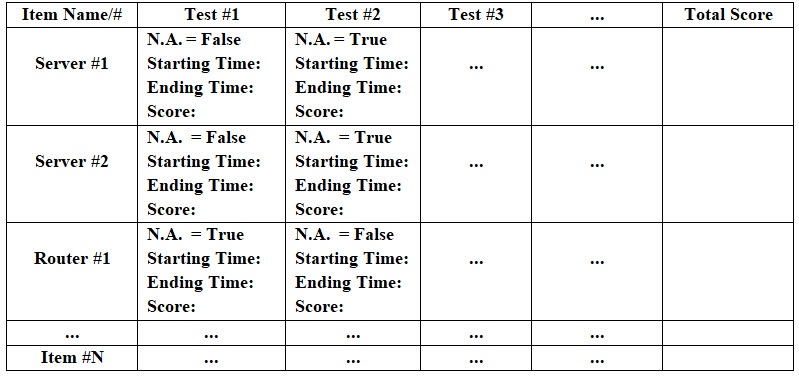
Image #3 Any item can be an entry in a logical as well as a physical unit. Therefore, we can check the physical or logical independently at our convenience. The scoring or performance is critical to our intelligent analysis and processes. The manual testing of these matrices must be manageable and doable by human. As for the machine testing, the sky is the limit to number and frequencies of testing as long as the testing does affect system performance. Virtualization can also play a big role in testing. We can clone the tested unit on a virtual server and run with such virtual server and perform anything we wish to test with such virtual independent server. Virtual testing would not interfere with system performance. Intelligence: To simply intelligence in our case, we are using the data we have collected from these matrices to run a number of scenarios (100 or more) and give each scenario a score or a grade. Based on the score, the machine would be able to make a decision, but in reality it is a calculated guess (100 or more). Since, we have the data for recent events plus history of previous events, then our machine would be able to perform cross reference, deduction, probability, decisions, statistics, reports and find frequencies, patterns and tendencies. Virtualization: Virtualization would give us the freedom to run applications, tests, ... etc independently with hardly any interference. Virtualization also gives us the ability to create almost endless number of virtual servers (if core memory allows) with hardly any effort. The release of these virtual servers are done with ease and the memory space used would be mopped clean with everything in it including viruses. Blueprint: Our Blueprint is Automation, Intelligence and Virtualization. Adam's Question Revisited: Our answer is: it must be done by man and machine. Our Intelligent Hackers Prevention Management (IHPM) System: Most Cybersecurity is done by monitoring and surveillance with hardly any intelligence or automation. Hackers are well funded and use Artificial Intelligence in their arsenal. In short, we are building a CRM and Big Data system to predict and anticipate any hackers' next attack. Virtualization, DevOps, DataOps, Machine Learning and automation would be used to automate prevention and remedy of hacker attacks such as Man-In-The-Middle Attack (MiTM), Distributed Denial of Service (DDoS), Botnets, IoT Based Attacks, spyware, Ransomware, viruses, worms, cross-site scripting, IP Spoofing, Eavesdropping, Phishing/Social Engineering Attacks, Data Leakage, ...etc. Our IHPM System uses implemented CRM and Big Data concepts and tools to build our Intelligent Prevention Management System. IHPM addresses and tracks hackers thinking, intentions, tools, approaches-scams, tendencies, support, locations, skill levels, operations, training, news and anything related to their attacks. Our IHPM's data would be treated the same way we handle Big Data and its processes. Our architect and design main ingredients are: Intelligence, Machine Learning, Virtualization, DevOps and DataOps, Testing Automation, Compression and Encryption, Hashing, Bit Mapping, Timestamp, Dynamic Cookies, Written Processes and Regulations, Human Tracking Reporting, User Verification, Reports, and Templates. Our IHPM Detection and Vulnerability Assessment Using Man and Machines: In a nutshell, how our Hackers CRM and Big Data collected can be used by man and machine. http://sameldin.com/SamQualificationPages/MachineLearning.html Our Dynamic Automated Intelligent Detection and Vulnerability Assessment uses what call "Zero and Ones" of hacking, patterns, matrices, data, statistics, risks, time factor, human expertise and constant updates to perform the detection and assessment. Our IHMP would have its own training for employees, users, security staff and any personal involved in security prevention. Prevention and Remedy are automated using intelligent management, documentation and testing systems to handle vulnerability, intrusion, detection, prevention, patching, verification, threats, protocol, scanning, data exfiltration, policies, processes and guidelines. Templates are automatically populated to speed the handling and processing. Our IHPM Risk Assessments Using Virtualization and Machine Learning Services: Our view of Cybersecurity risk Management in the case of cyber attacks regardless of the size of the attacks is: how our Risk Management processes and tools would eliminate or minimize the damage of the running operations-system, hardware, software, data and processes? Using Virtualization to build small (with short lifecycle - no nesting) and manageable virtual services including data would reduce and eliminate the risks of downtime to the system major components or bringing these components to a halt. In short, we would be reducing the size of the system running components into smaller-virtual manageable components. The assessment of these small manageable virtual servers (with services) would be easier, faster and controllable than that of big size system components, tiers and nested components. Machine Learning would performs the creating and testing of these virtual small manageable servers (with services). There is no guessing which component is running on the system. Detection: What we believe Cybersecurity today is performed by monitoring the running networks looking for issues and any irregularities. In short it is a guessing game until something attacks are detected. In the case the AWS DDoS Attack in 2020 and customers were the ones who reported the issues to AWS. We believe pre-detection runs should be done in the following steps: 1. Automatic polling of every item on the networks on set schedule 2. Manual polling and monitoring of the networks 3. Both manual and automated Cross reference of both automation and manual polling 4. Scheduled reporting of the above steps 5. Scheduled detection (false positive and false negative) analysis 6. Constantly creating new virtual services with new virtual IP addresses 7. Services should not run for long time 8. Cloning and testing services-virtual servers for vulnerability on scheduled basis 9. Grading the performance of the above steps - feedback The above Pre-Detection list should help in detecting any attack. In case of attack happens, then Vulnerability Assessment should be performed. Vulnerability Assessment: Once intrusion is detected then prevention steps and vulnerability assessment should be performed. Prevention steps are based on the type of intrusion. The key of Vulnerability Assessment is not be defenselessness, secure all weakness, not escalating the intrusion further and closing all the gaps. Automating Vulnerability Assessment can also be done using preplanned processes and documentation. Documented lessons learned is also part of Vulnerability Assessment. Risks and Risks Handling: Pre-calculated risks and risks handling are critical to the running system, the business and the handling of different situations. Automation can be used to get the ball rolling (phone calls, emails, alarms, steps, processes, documentation, restarting networks, rerouting, backup and rollbacks) and no guessing game. Fixing the Issues: Apply the needed fixes Lessons learned Rollbacks: The timeframe of rollbacks and resuming the business operations would be automated and very short. Rollback would be as easy as restarting these small and manageable virtual services-servers with new virtual IP addresses. Using Virtual IP addresses would make it more difficult to track or reused by hackers. These virtual servers would be deleted completely and any hackers code would be deleted also. No chance of hackers' code to pass to another component. Our Recovery: Assessments of damages and the risk of attack reoccurrence would be handled by Machine Learning Services. Our IHPM would automatically alert security staff with what-where-how the attack, risks, step-by-step handling processes and the impacts. Risk Documentation are automically created and populated. Zero-Day Attack, Reverse-Engineer Code and Internal Hackers: These attacks can go undetected for a long period of time. As a solution architect, our approach and architect uses our Intelligent DevOps and DataOps services to create the following: 1. Multilayer Architects-Tiers (clients, proxy, web handlers, Business, services, engines, utilities, common, data services, data storage, filing system, batch processes) - each tier would be running as an independent virtual server 2. Dedicated Virtual servers (for each tier) with bare-metal support 3. Virtual independent data services servers - data must be an intelligence service and not a dumpy storage 4. Use of Secured Buffers - For speed and security 5. Use of Virtual Intelligent Business Brokers (handle business objects and services) 6. Mail security 7. Audit trail and log of every user and request 8. Automated Virtual Testing 9. Patch code are zipped and encrypted with passwords plus scanned for issues (using Machine Learning) 10. Machine Learning to handle detection, alarm, prevention and remedy Note: we do not expect that companies would be able to change their existing system to implement our recommendation, but building an intelligent DevOps which would create Dedicated Virtual Servers (for each service and each tier) which can be implemented with minimum effort and time and their lifecycle should be short and deleted totally at the end of their tasks. |
|---|