
|
Sam Eldin - IT Profile |
|---|
| Home | CV - Resume | Tools 4 Sharing | Architects 2 Show | Big Data Presentation | Android Training | Java-Unix Code Templates | Interviews QA & Code |
|---|---|---|---|---|---|---|---|
|
|
|
Where Can We Find Real Investors? (Linkedin Post) 
|
|---|
|
Our Entrepreneurial Two Cents Worth for Investors • The Negative Side of Working with Investors • What are the Main Issues? • What Problem We are Aiming To Solve? • Investors FAQ • Our Security System • How can we go about building our Post Office? The Negative Side of Working with Investors Starting my article with negative comments may not be appreciated by most readers, but sadly to say my experience with investors has not been the best. A number of investors did not answer my calls or emails after six months of working with them and giving them business plans, market research, prototypes and code. It seemed that once they had the project, they did not need any more of my free services. They could have taken all my work and outsource the project, without ever consulting me. I had no way of knowing since they cutoff our communication. One investor had an unqualified technical person to evaluate my project and talent. The worst investor was asking for $30,000 insurance deposit to transfer $44 million to our shared business account which I created. The $44 million would have been used to develop and market two projects, Credit Repair Data Warehouse and Paperless Lending System, which I still have the signed contracts for. Not to mentioned, most of these investors seemed to be searching for free ideas to build, and they were taking us for the ride and milking us out of whatever they can. Afterward, I started asking for cash in advance for my summary business plan, where they never bothered to call or email. As for the legitimate investors, they give me the feeling that they are doing me a favor and not acknowledging the fact that without my ideas, thinking, knowledge, experience, passion, tools and effort, there would not be a project nor would there be any return on the investment. Definitely their funding is needed and I do appreciate their effort, guidance, and time. I always look at working with investors as a team effort, where all the parties bring their fair share to make the project a success. What are the Main Issues? Let us look at the top three. #1: Cyber Security Market According to the Forbes magazine, cyber security is expected to reach $170 Billion by 2020. 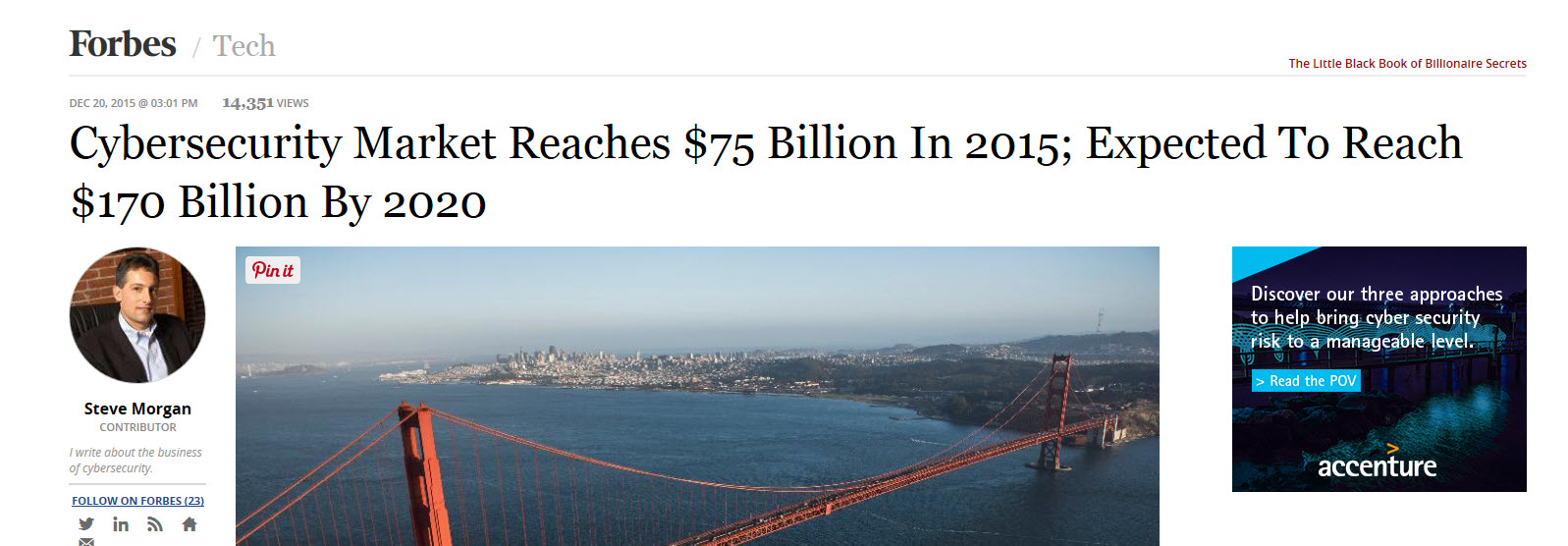
#2: Big Data: The challenges that businesses face is making use of data that is growing at an exponential rate. #3: Cloud, Mobile and Database: Wireless data (signals) is an open invitation for the taking, and cloud is the same where data is being transmitted between hosts and service providers. Databases are target practice for internal and external hackers and employees. What Problem We are Aiming To Solve? We are building a Data Farm in the cloud plus the mobile part of it. Our CRM Data Farm (our Post Office Project) would handle Security, CRM, Big Data, Business Intelligence (BI), Analytics, Intelligent System, Data Stream, Governance and end-to-end solution. Investors FAQ What are our investors investing in? Our Post Office project is composed of the following subsystems or services: • Security using Compression-Encryption • Data Services • Intelligent Data Analysis Each can be sold separately or combined with other services, and can be easily integrated with any existing system. We believe our best seller is Security using Compression-Encryption. The question is "Why". It will put hackers (internal and external) out of business and will change how to build security. Our conceptual model would leave unauthorized infringers puzzled and unable to access our compressed encrypted data. What is the goal of our Post Office project and how can it be achieved? Our Post Office Project's architecture is based on the following concepts and approaches:
The following matrix outlines which approach strategy and processes would be paired with each service. 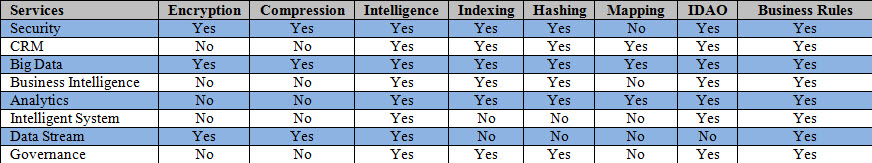
Our Dynamic Business Rules is the key in making system changes without modifying any code or processes. Our Security System Our Security System uses algorithms which can compress files or data (Lossless) to more than 65% of its original size. Lossless compression is a class of data compression algorithms that allows the original data to be perfectly reconstructed from the compressed data. Our algorithms run as fast as CPU speed and we can also create a security chip with its own CPU, memory and Math Coprocessor for faster performance. Each chip would have its own unique IP Key that maps each client's IP address/Mobile ID into an internal storage cell/register. The IP Key is used in compression-decompression-encryption-decryption code. The IP Key can also be dynamically loaded and changed for adding an additional level of security. Our Security Gatekeeper Our Security Gatekeeper can be a chip or software which receives only certain types of signals or files which has the client's IP address. Our Security Gatekeeper will identify the incoming data or signals and check for authentication and authorization. It would perform compression-decompression- encryption-decryption code on these files or signals. Our Gatekeeper can be turned On/Off and the connection would return back to the client's original security setting. What will our Compression-Encryption replace? • Secure Sockets Layer (SSL) • Hypertext Transfer Protocol Secure ( HTTPS) • Firewall • Any security software How can we go about building our Post Office?
|
|---|