

|
Object Oriented Cybersecurity Detection Architecture (OOCDA) Suite |
|---|
|
|---|
|
Sam vs AWS
What is AWS? Amazon Web Services (AWS) is the world's most comprehensive and broadly adopted cloud platform, offering over 175 fully featured services from data centers globally. Millions of customers including the fastest growing startups, largest enterprises, and leading government agencies are using AWS to lower costs, become more agile, and innovate faster. AWS Components:
AWS Testing: Independent, third-party testing providers also provide testing as a service on cloud resources. What is Sam Virtual Integration? In a nutshell, Sam Virtual Integration is Homegrown Java-Cloud based components which are added to any existing infrastructure and platforms. (see http://sameldin.com/SamQualificationPages/VirtualIntegrationPage.html) Sam Virtual Integration Platform Components:
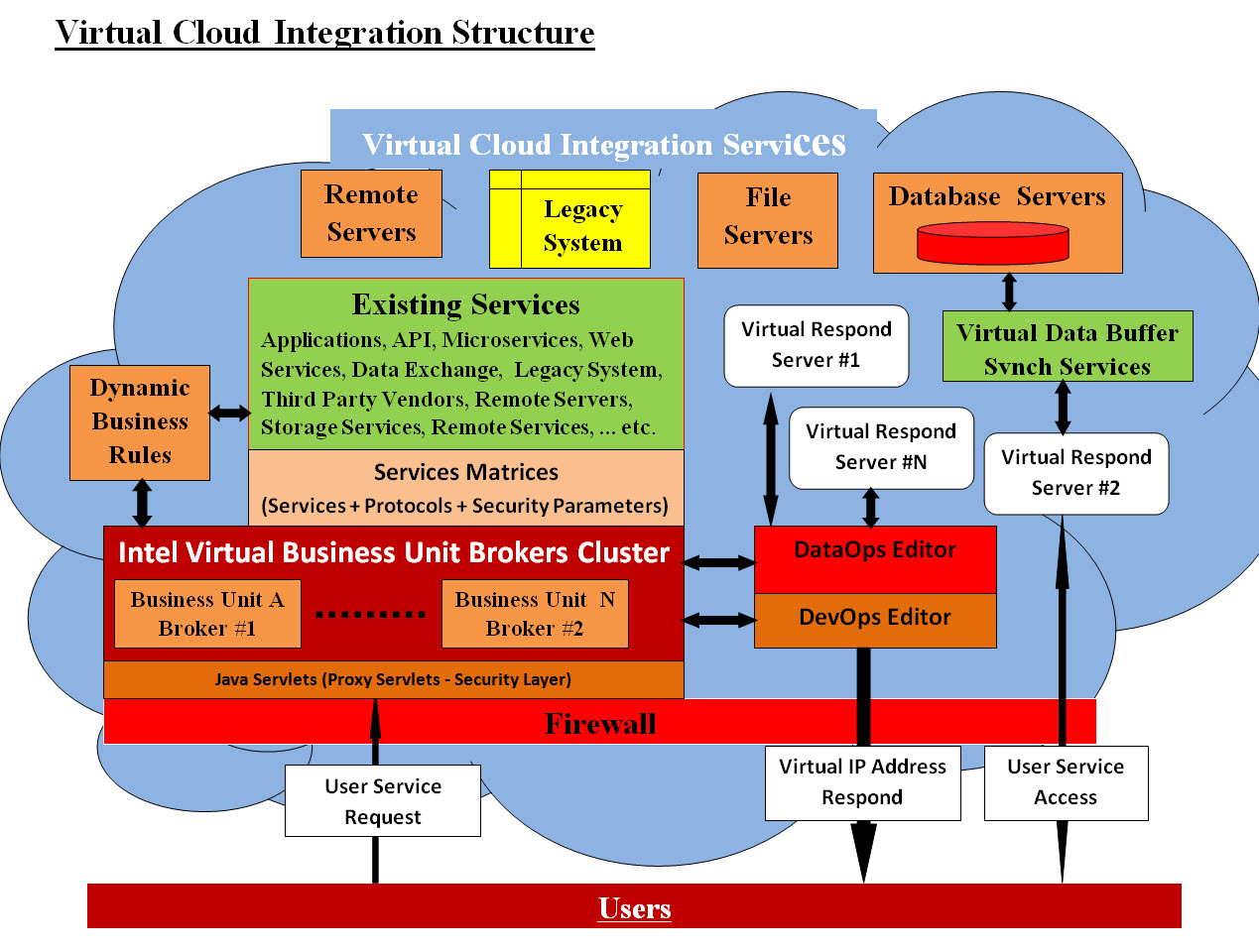
Image #1 We recommend that visitors checkout our Virtual Integration page and see the details of our architect. In Image #1, we only added the following components to any existing cloud system. These components are Java Based code: • Intelligent Business Unit Brokers Cluster • Virtual Data Buffer Synchronized Services • Services Matrices (Services + Protocols + Security Parameters): • Dynamic Business Rules • DevOps • DataOps • Audit Trail Our Security: Looking at Image #1, users would be making stateless requests which go through the following security layers: 1. Firewall 2. Java Proxy Servlets 3. Intelligent Business Unit Broker security 4. Services Matrices security parameters 5. Virtual Server (container) 6. Virtual IP Address 7. Virtual Data Buffer Synchronized Services AWS Replacement: Looking at Image #1, the following are steps of AWS Replacement :
Our Virtual DevOps-DataOps Containers Support verse Virtual Monolithic (Big Container) A monolithic architecture is building a large system with a single code base and deployed as a single unit, usually behind a load balancer. It typically consists of four major components: a user interface, business logic, a data interface and a database. We believe creating a virtual system or a virtual server which encompasses more than one application or services is also a monolithic system or server. Pros and cons of a monolithic architecture is leading software vendors to develop more smaller and concrete services such as Microservices and Docker platform. Docker is an open platform for developing, shipping, and running applications. Docker enables you to separate your applications from your infrastructure so you can deliver software quickly. With Docker, you can manage your infrastructure in the same ways you manage your applications. Our DevOps, DataOps Approach and Vertical and Horizontal Scaling: We view any services (Microservices, web Services, Legacy System, Applications, third party software, ..etc) as a service. Each service must run independently (stateless, Loosely Coupled, with its supporting services) within a Virtual container Server with its own Operation System and supporting software. Data (database, filing system and/or Legacy system, remote support, ..etc) would be created by DataOps as a Virtual supporting container also. The lifetime of our virtual containers (service and data service) would be the life span of the requested service. This means the checking account request in Images #2 would end and all of virtual container including the operation system and possible the hacker code would be wiped clean for next service request. As for DataOps Container, there must be some kind of end of job or house cleaning to make sure data is updated properly and secured. The DataOps container would be wiped clean also. 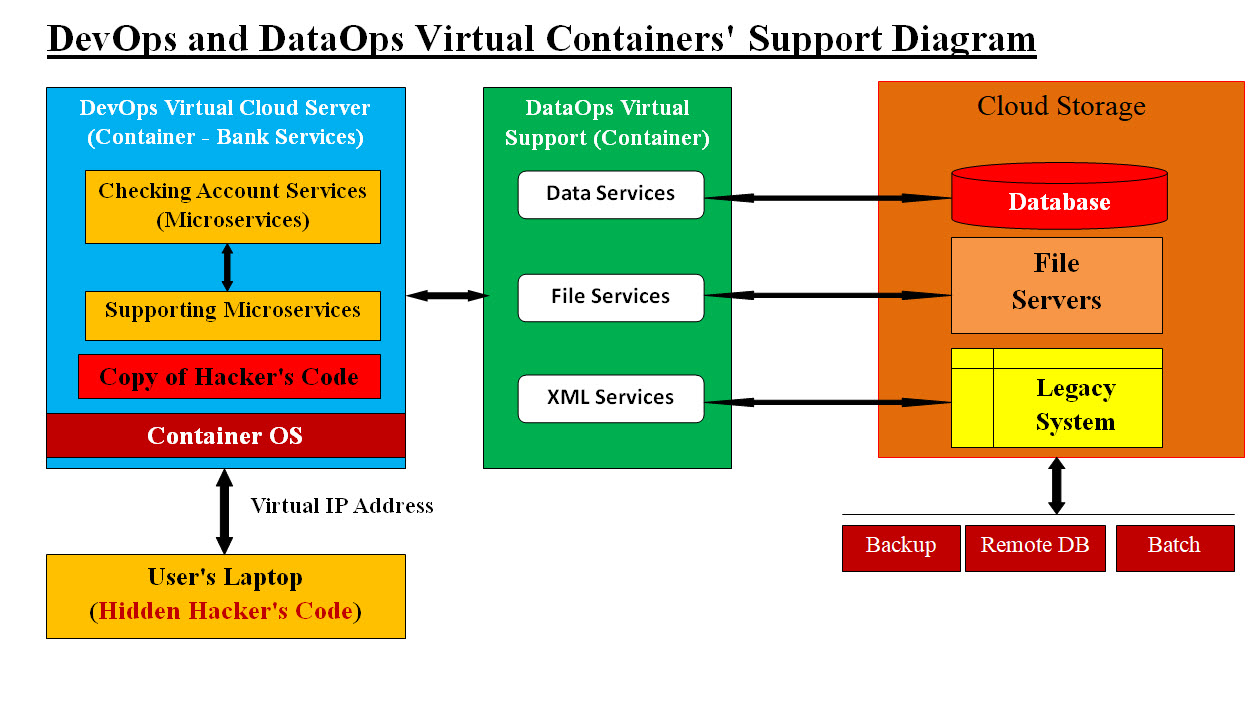
Image #2 Image #2 presents our approach to monolithic architecture where Our DevOps and DataOps would be creating the virtual servers for helping each service to run (stateless, Loosely Coupled, with its supporting services) within DevOps and DataOps containers. See the following Bank's user request scenario. Let us look at a Bank user request scenario: Let us assume a bank customer is requesting bank services plus this bank customer has virus on his/her laptop. Our system would be creating a virtual server (only exists in memory) as a container and it contains a virtual bank service application as a component running within the virtual server. The virus main objective is to copy itself on the server for further attack. It also has the Virtual Server IP (in our case it is virtual IP address) address which the virus would use for future attacks. Regardless of the virus objectives, the virtual server, the virtual bank server application and Virtual IP address would be completely deleted from memory once the virtual bank service application is done. VIP address would also be deleted so no tracking or further attachs would be possible. The Virtual Data Buffer Synchronized Services would also protect the internal data structure and access from an unauthorized access. Performance of Our Virtual DevOps-DataOps Containers Support: The creation and end of job house cleaning must be automated with no human interface. Queues of ready Virtual containers with each has its own operating system and virtual IP address can be created to speed the performance of system. This is the Horizontal Scaling of any running services. As for Vertical Scaling would be done by proving enough memory for any service with its supporting software to be running within the DevOps container with no issues. Sam Virtual Integration verse AWS: We need to present the following points and give credits to AWS as we see them: • CEO, stakeholders, managers and tech leads must make difficult decisions including cost • AWS is an easy choice since these decision-makers would be passing the risks onto the AWS • The Return on the Investment (ROI) would have less risks and their headaches are gone • Sam Eldin is a One-Man-Show without any credentials and only offering Sam's architects, templates and frameworks • AWS support can be counted on, but it comes with a price tag • .. etc Most companies have and run their existing infrastructure, development-testing environments and software licenses, .. etc. These are companies' assets and they may have invested heavily in such assets. What would be AWS cost of the following? • Using AWS infrastructure • Development • Storage and Batch Processes • Third party testing • Integration • Daily Charges • Support • Upgrade • Security • Sam's Checklist Sam's Checklist of processes and steps in building and testing Sam's Virtual Integration. Planning: • Business size (Small, medium and large scale + enterprise level) • System Plans ( 1, 5, 10 yrs) • Long and Short Term Investment • Management Structure and Templates • Technologies • Risk Analysis • Cost Analysis • Budget • Documentation Existing Structure: • Infrastructure • Storage • Batch Processing (cost) • Distributed System • Presentation Zone Firewall • Secure Zone Firewall • Baronet Zone Firewall • Security Existing Platforms: • Bid Data - structured and non-structured data (PDF, excel, images. ..etc) • CRM • Analytics • Business Intelligence (BI) • Legacy System Software and Tools: • Frameworks • Services • Development • Reusability of code • Common, utilities, services • Reports • Templates • Errors and exceptions • Audit trail • logging • Tracking • Parsers • Convertors • Data Exchange • Social Media support • Dictionary Existing Support: • Support • Online help • Customer service • Training Target Performance: • Customization • Performance • Speed • Flexibility • Availability • Refactoring • Transparencies • Latencies • Scalability • Reusability • Support • Recovery • Rollback • Backup System Integration: • Virtualization • Intelligence • Automation • Integration • Security Testing: • Virtual Testing • Test Resources • Testing Plans • QA • Documentation • Training |
|---|