

|
Object Oriented Cybersecurity Detection Architecture (OOCDA) Suite© |
|---|
|
|---|
|
Object Oriented Cybersecurity Detection Architecture (OOCDA) Suite©
OOCDA Suite Start Our Challenge of Turning Cybersecurity Detection Into an Exact Science: Security might not be an exact science, but now it is a branch of computer science. Medicine, despite the popular belief, is not an exact science. Our attempt or challenge is to build a Cybersecurity detection structure where we would be able to perform accurate quantitative expression or precise predictions and rigorous methods of testing. Definitions Computer Security, Cybersecurity, or Information Technology Security is using technologies, processes and controls to protect systems, networks, programs, services, devices and data from any cyber attack. Our Tools: Automation, intelligence, virtualization and virtual integration are our basic tools used to develop any of our cloud system. What is cloud computing? Cloud computing is the delivery of computing services including servers, storage, networking, software, over the Internet. We as architects no longer think except in cloud. Cloud also includes mobile Apps services and the security associated with these services. Note: • Any network with HTTP server or an internet server is a cloud. • Cloud Infrastructure is the base for DevOps and DevOps is the foundation for any Cloud system. What is Object Oriented Design (OOD)? OOD is the thinking and the creating of an object which would solve problems. OOD main objective is reusability. Our job here is not to teach OOD, but use OOD to solving our Cybersecurity detection issues and cash-in on the object's reusability. What is Object Oriented Cybersecurity Detection (OOCD)? OOCD is an object which performs Cybersecurity detection. Therefore, we need to think and create OOCD object. Cybersecurity detection is not a simple task nor has one answer, but structuring detection into an object with tools and methods is the perfect base to build on. The following link is our Object Oriented Cybersecurity Detection (OOCD) webpage: 1. Object Oriented Cybersecurity Detection (OOCD) Our Cloud Object Oriented Cybersecurity Detection (OOCD) Architecture Suite: What is Our Cloud Object Oriented Cybersecurity Detection (OOCD) Suite? OOCD Suite is: A multitier cloud system with intelligent and virtual components which we had architected-designed to secure End-2-End any cloud system from internal and external hacking attacks. Security is implemented independently by each tier. OOCD Suite is scalable, integrate-able to any cloud system. Image #1 represents our 2,000 foot view. 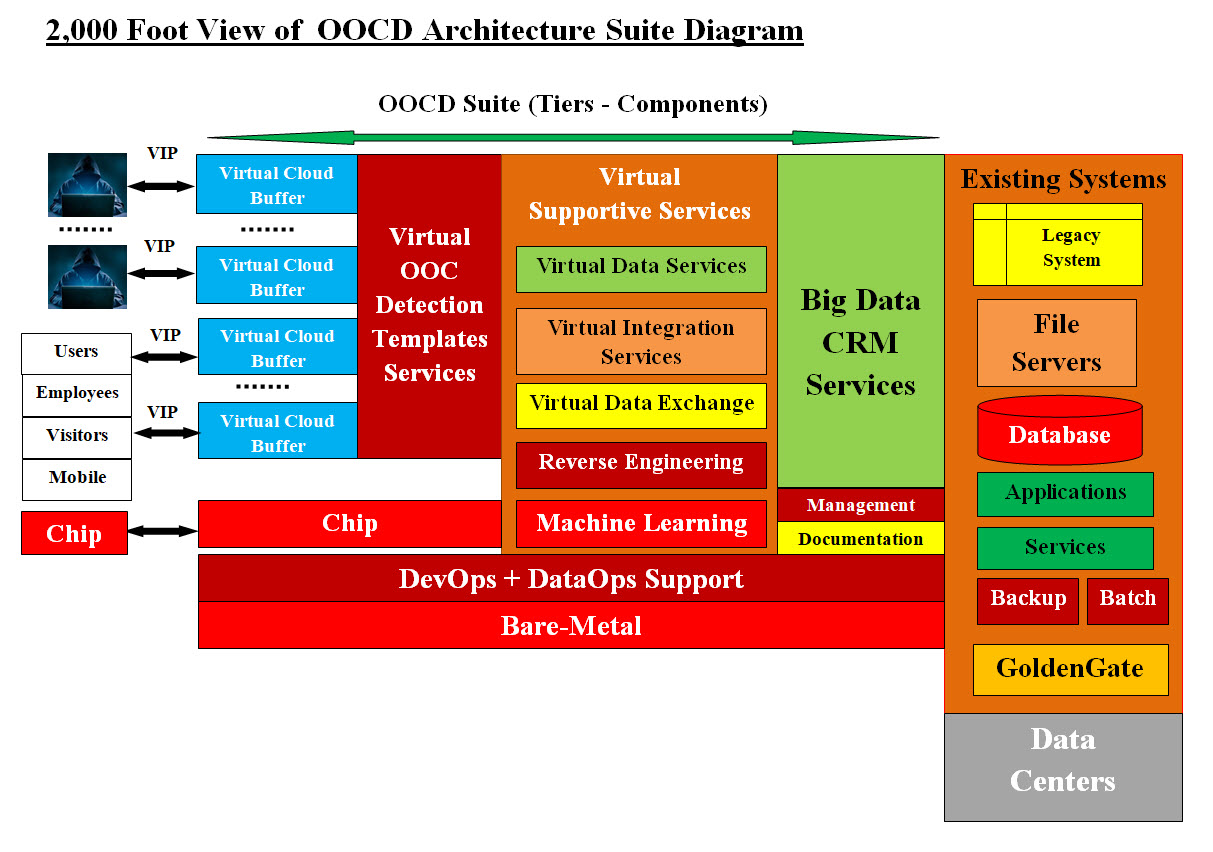
Image #1 Image #1 represents three views: • The outside would including millions of hackers • Our OOCD - tiers and components • Any existing cloud system which our OCCD Suite would be protecting Performance and Scalabilities will be covered in the following sections. Our Cloud OOCD Suite Architecture - Structure is: The following links are the architectural-design for each of our system components. 2.0 Cloud Tiers - 2,000 ft view of the system components 2.1 Virtual Cloud Buffer 2.2 Virtual OO Cybersecurity Detection Templates Services 2.2.1 Malware Detection Template Analyis 2.2.2 Phishing and Spear Phishing Analysis 2.2.3 ID Protection Toolbox (SIPBox) 2.3 Virtual Supportive Services 2.3.1 Automation, Intelligence, Virtualization - Adam's Blueprint 2.3.2 Machine Learning 2.3.3 Intelligent System 2.3.4 Virtual Integration Services 2.3.5 Sam vs AWS 2.3.6 Reverse Engineering 2.3.7 Excel-DAO-XML Data Exchange Seed Framework 2.3.8 Virtual Data Services - Database Replacement Using XML 2.4 Big Data Services 2.5 CRM Services 2.6 Management 2.7 Documentation 2.8 Testing Plans 2.9 OOD Testing 3.0 Chip-2-Chip Services 4.0 Existing Systems 5.0 DevOps - Infrastructure Support 6.0 DataOps - Data Services 7.0 Bare-Metal 8.0 Vertical Scaling of Data Centers 9.0 Frequently Asked Questions (FAQ) OOCD Architecture Suite is an End-2-End architecture with partial-detailed design and Java code. The goal is to build a cloud Umbrella for big enterprise systems with room for Vertical and Horizontal scaling. OOCD Architecture Suite is a cost effective homegrown system with or without any vendors support or outsourcing. Infrastructure support (DevOps) and Data Services (DevOps) are the bases for developing, automating, securing, adding intelligence and integrating OOCD Architecture Suite. Vertical and Horizontal Scalabilities Our OOCD Suite is composed of a number of virtual tiers and virtual components. Creating or deleting any number of tiers and their components can be automated. Creating any number of a specific tier and their components can also be created on the fly to handle traffic loads. For example, Big Data and CRM Services may not be required by clients with limited number of customers or services. Our OCCD suite Virtual Cloud Buffer creations and deletions would be automated to handle malware attacks. Machine Learning support would be combined to deter DDoS Attacks. Vertical Scalabilities: Each virtual tier would be able to vertically create any number of its components to increase performance, speed and handling different requests. Horizontal Scalabilities: One of more Virtual tier can added as needed to increase performance, speed and handling different requests. The best example of Horizontal Scalabilities would be (as in the case DDoS Attack on the Russian tech giant Yandex - the biggest DDoS Attack ever) performing the following:
Performance Performance would measure by the performance speed of the detection protection and the creation of detection-protection itself. Only the needed virtual services or detection objects would be created. All the services and detection objects are virtual and scalable. The newly discovered hackers' IP addresses or malicious code be used immediately by OOCD inheritance features and no need to depend firewalls or any vendors support. |
|---|