

|
Case Study - Electric Vehicles© |
|---|
|
Case Study - Electric Vehicles
We are using 2022 Tesla Model Y as our electric vehicle Case Study. 
Image #1 Introduction: We need to handle this case study of electric vehicle the same way we would handle any network. The main object of any network is to keep the network performing its core job. Virtualization, automation, intelligence, integration and Machine Learning are what we need to use to help run any network as well as electric vehicle. Our Goals: This case study is to develop the needed software features which: • Protect the vehicle o Theft o Hacking • Dynamic update of each software components • Track each component • Audit trail each component • Track each component performance Therefore, any component which produces and consume data is what would be handling and protecting. We need to assess this car and figure which component has intelligence and produces data and type of data produced. We also to add intelligence and Machine Learning support to each component. It should have a management system and backup system for rebooting failed system. For example, the car main power supply is the battery, therefore such power supply or the battery has to have Intelligence to: • Give signals and direction to maintain the energy level • Should be able to sense errors and hacking • It must have tracking • Emergency handling processes This case study covers the following: • Car Features • Software Components • Data • Updates • Machine Learning • Machine Learning Pros and Cons • Intelligent Components (Supportive Intelligent Decision-Making) • Electric Vehicle Thefts • Security Types • Machine Learning Support Car Features BASIC INFORMATION: • ENTERTAINMENT AND INSTRUMENTATION • SAFETY AND SECURITY • COMFORT AND CONVENIENCE • SEATS • WHEELS AND TIRES • LIGHTING • ACCESSORY PACKAGES • BRAKING AND TRACTION • STEERING Tesla Model Y Sensors 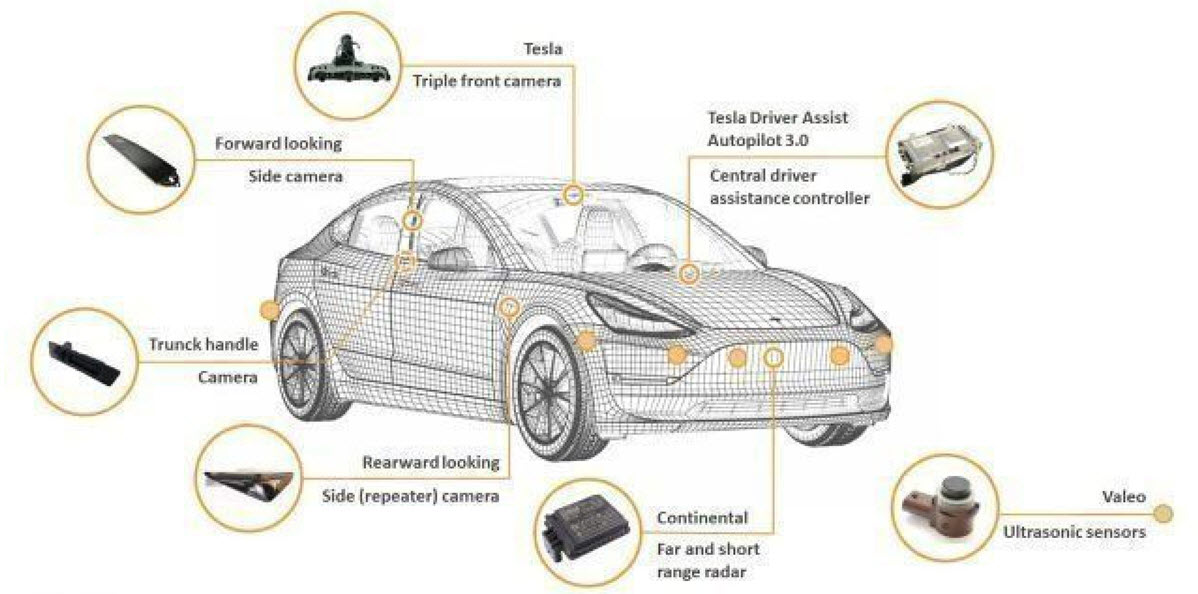
Image #2 Image #2 shows Tesla Model Y Sensors which are the biggest producers of data. Such data needs to stored, parsed and analyzed. Vehicle's Sensor's Type: Ultra-sonic: An ultrasonic sensor is an electronic device that measures the distance of a target object by emitting ultrasonic sound waves, and converts the reflected sound into an electrical signal. Ultrasonic waves travel faster than the speed of audible sound plus such sound humans can hear. Radar: Radar sensors are conversion devices that transform microwave echo signals into electrical signals. They use wireless sensing technology for detecting motion of objects and figuring out the object's position, shape, motion characteristics, and motion trajectory. Light Detection and Ranging - LiDAR LiDAR stands for “Light Detection and Ranging” and its technology allows self-driving vehicles to make calculated decisions with its ability to detect objects in its immediate environment. It can be thought of as a vehicle's “set of eyes” and the most important component in making self-driving vehicles a reality. Cameras: Cameras are image sensors and can automatically detect objects, classify them, and determine the distances between them and the vehicle. For example, the cameras can easily identify other cars, pedestrians, cyclists, traffic signs and signals, road markings, bridges, and guardrails Software Components We are presenting two use cases in our Virtual Edge Computing with Machine Learning. The cases are: • Electric Vehicles - this page • Autonomous Vehicles The Electric Vehicle case is the basis for Autonomous Vehicles case, therefore we do not want to duplicate the effort and the presented material. Electric Vehicles are totally run by software and we are proposing an intelligent virtual approaches with cloud support. We recommend that for the Software Components, the readers need to visit the Autonomous Vehicles page: Autonomous Vehicles© Data and Updates The reasons we used in the Software Component Section are the same for Data, Updates and Machine Learning Support sections. Machine Learning Support Main issues: It is very difficult for our small company (CRM Data Farm Corporation - CDFC) to prove that the existing Machine Learning tools and solutions is nothing but a guessing game using countless numbers of algorithms plus when these endless algorithms fail, then data is fixed to fit the patterns and algorithms. The following links have documented pages of our Machine Learning approaches, tools and copyright: Object Oriented Cybersecurity Detection Architecture (OOCDA) Suite© Machine Learning© Machine Learning Analysis, Data Structure-Architect© Machine Learning Pros and Cons We are turning Machine Learning into a science and not a guess game of trials and errors using algorithms. Cons: In short, Machine Leaning Cons is a "bottomless pit" with no return. Pros: We believe that Machine Learning would be running in the background of every application as an intelligent supportive decision-maker. How can we turn Machine Learning in to intelligent supportive decision-maker? Once we have data and we also have patterns related to the data based on the business case (Zeros-Ones), then computer can be trained to use the patterns to parse the data and find answers to problems, trends, correlations, frequencies, and so on. Again we are using Zeros-Ones of the business cases to build patterns - see my Machine Learning pages. Virtualization: To help with reducing the loads and the overhead on any running system, virtual system or servers can be created on the demand to help create the needed Machine Learning tools to run in the background as an intelligent supportive decision-maker. Virtual Edge Computing - onsite analysis and offsite learning: We recommend the creation of Virtual Edge Computing Servers or System with Machine Learning. Each Virtual Edge Computing Server-System would have to work with one and only one component. For example, in case of electric vehicles, one Machine Learning Virtual Server (we call it VML_ TPMS, see Intelligent Components section) would be created to hand Intelligent Tire Pressure Monitoring System (Intelligent TPMS) and works only with TPMS. The data collected would be would be parsed-analyzed by VML_TPMS plus data is compressed-encrypted and send to the cloud for further on site evaluation and learning. The new found issues and solutions would be a new update to the Machine Learning tools installed on the car computers. Intelligent Components (Supportive Intelligent Decision-Making) Intelligence and Intelligent System: We as human beings, when addressing anything as intelligent, we are implying that it has human-like characteristics. Therefore, Intelligent System is the ability of a software system to have human-like characteristics and do the following: 1. Plans 2. Performs abstract thinking 3. Understanding - parse, compare and search 4. Solves problems 5. Does the footwork 6. Gives choices 7. Communicates 8. Self-awareness 9. Reasoning & Learning 10. Retraining - self correcting Assume that each category is equal to 10% of intelligence, then we can scale the actual percentage of intelligence of any software system. We have the know-how and the architect for developing 100% Intelligent System. Intelligent Components (Supportive Intelligent Decision-Making): To define intelligent components, let us look at Intelligent Tire Pressure Monitoring System (Intelligent TPMS) Intelligent Tire Pressure Monitoring System (Intelligent TPMS): Intelligent Tire Pressure Monitoring System (Intelligent TPMS), which not only gauges the air pressure of tires, but also accurately identifies road conditions and tire motion across the road surface. Combined with sideslip prevention systems, is another advantage of the new system for the integration of tire pressure monitoring and sideslip prevention into a single system. Machine Learning and Intelligent Components: Note: Our Virtual Edge Computing uses our Case Study - Electric Vehicles as a part of its presentation. Looking at Intelligent Tire Pressure Monitoring System (Intelligent TPMS Image #3) and its features, we see that it has ability to integrate the tire pressure monitoring and sideslip. This means that it generates data where data can be used by Machine Learning tools to learn as data is collected. Therefore we can add the specifically needed Machine Learning tools to run in the background to help with the decision making of the Intelligent TPMS. 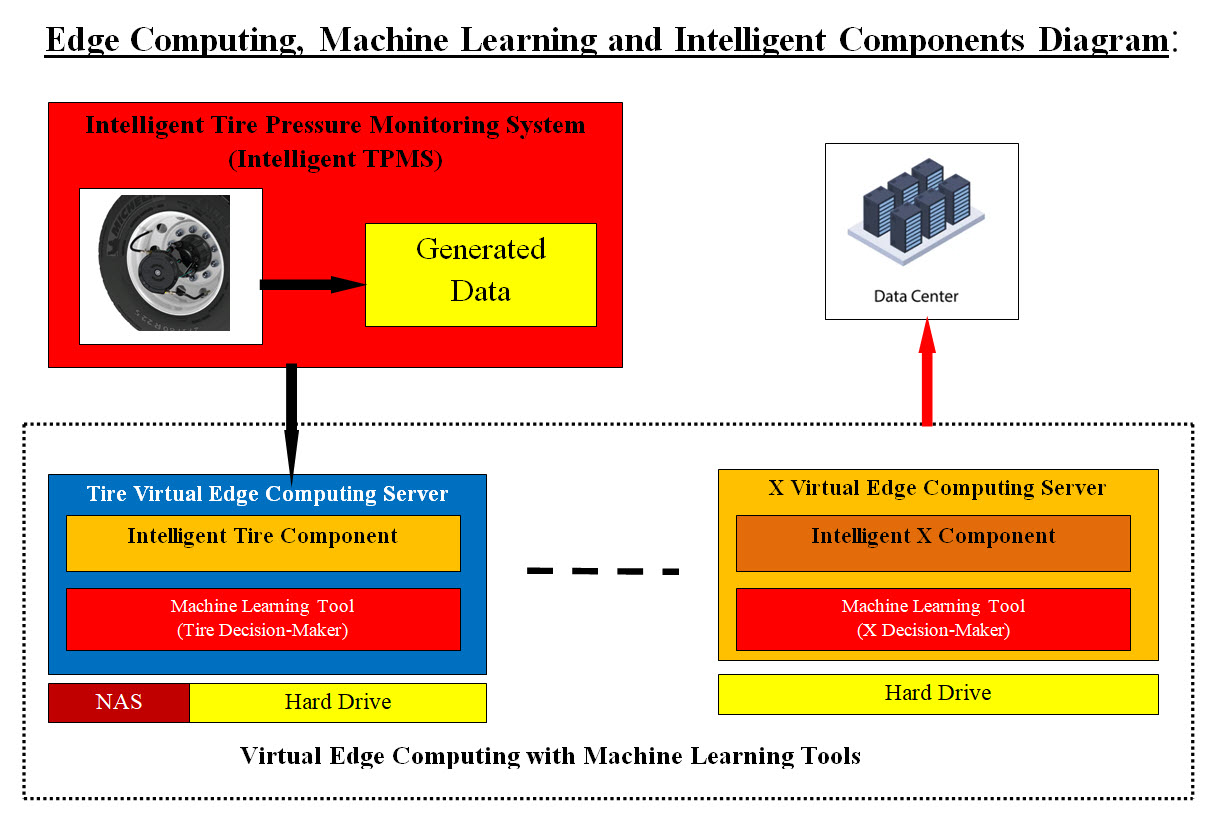
Image #3 Image # 4 is showing how Edge Computing can be implemented by creating a virtual server (Virtual Edge Computing Server) as a dedicated virtual system to help with monitoring and supporting any intelligent component. Electric Vehicle (EV) Thefts As Electric Vehicles are getting more electronically sophisticated and so do hackers and thieves. Searching the internet for how to hack, stole, break into, damage or just play a joke or prank on electric vehicles would result in numerous ways and what electronic gadgets are needed and how to buy them. As for using phone Bluetooth as a car key, there are a number of Bluetooth tracker which is a little gadget designed to track an item when it's attached to it or sitting inside of it. Also called a "key finder" or "electronic finder", they're essentially a device that uses wireless signals to pinpoint the location of the thing they're next to or inside. EV charging stations are surprisingly vulnerable to cyber attacks from hackers. The risk of EV hacking rises as more and more charging stations are becoming common than before. Security Types Cybersecurity for EV is also covered by Autonomous Vehicles page. As for Bluetooth or WIFI, we recommend a quick solution to stop hackers and thieves for having copies of your key code as follows. Building a Security Key Using Frequencies, Time of the Day and Password Combination: For Bluetooth there is 1600 frequencies (hopefully more than 1600 would be generated) which Bluetooth devices can hop. We are proposing a possible key combination for every 30 second of the day would be to used as passwords. In a nutshell, the following is the combinations: One day = 24 hours = 86,400 second = 2,880 (30 second) A different password for every 30 of the day = 2,880 password A different frequency used for every 30 second of the day = 2,880 frequency use This means if the hackers gets a security key value at 4:31:26 PM, then the security key will change after 30 second to a different frequency and a different password. This would not give the hackers or the thieves enough time to get to the car and then try to open it with the security key which they copied. The only way these hackers or thieves would be able to open the car is having the car key or mobile or electronic watch connected continuously. 30 Second: We choose 30 seconds as a time interval of changing the code, so would not give hackers or thieves enough time to use the code. At the same time car owners would only have to wait for 30 second for the car and the code be synchronized. We would need to build a matrix with - possible size 2,880 digital data rows: Time - every 30 second -total number is 2,880 Frequency - one out of 1600 (or more) Bluetooth frequencies Password - one out of 2,880 possible password This matrix would be copied to the car key, phone, watch. Such matrix can be developed using algorithms. Both car and key or phone would have the option to updating the matrix into a new one with a new set of passwords and frequencies. The digital matrix's size would be easily fit in any electronic car key. The key may requires a day timer. If the hackers are using Machine Learning to figure out how to find or build a security key, then they need would figure out the possible security key in the following combination: 2,880 Seconds (to power of 2,880 password) (to the power of 2,880 frequency) such a number will take sometimes to have the possible or correct answer using the fastest computers. The car and phone or key must be synchronized to work and car owner may have to wait 30 second for car and key to be synchronized. |
|---|