|
|

|
Sam's Total Picture and Hackers' Summing Pool
|
|
|
|
Sam's Total Picture and Hackers' Summing Pool
This webpage is awake up call to the cyber wars and hacking which is becoming a Powerhouse. There
is a lot of answers but which one is optimum. We will put a picture of what
we believe the major issues and our answers.
Existing Tools and Hackers' Summing Pool:
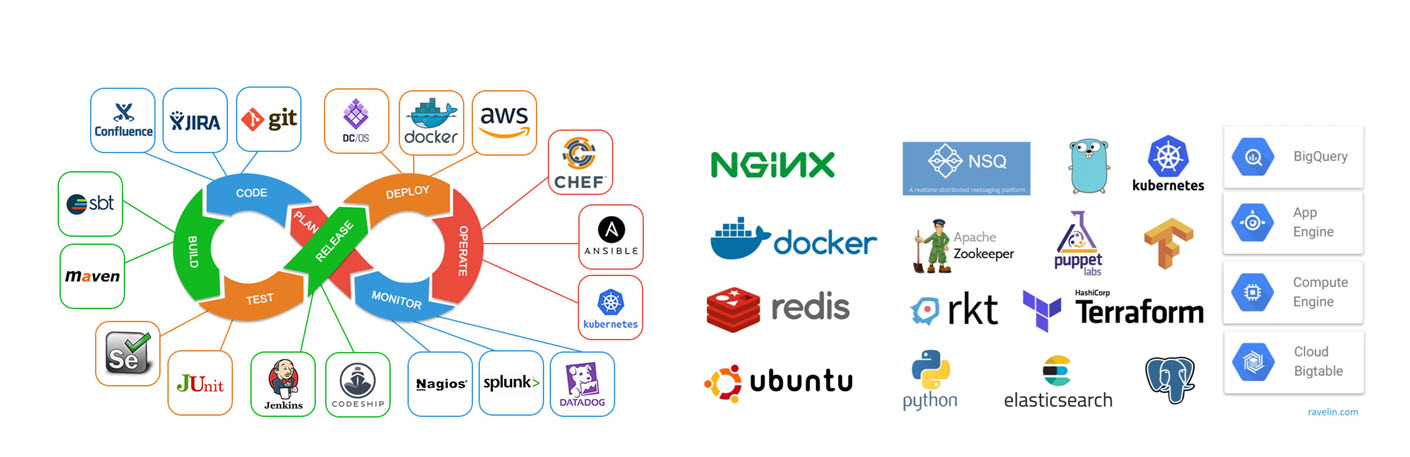
Image #1 - Hackers' Swimming Pool
Image #1 is what we found on the web which presents the existing tools
used by the IT and Infrastructure teams to build their secure system. The
table at the end of page has quick definitions of what most development teams use.
Looking at the tools table and with the assumption that each tool may have
thousands of software files as their distributed products.
33 Vendors * 1,000 files * 100 update * X misc files > millions of programming code files
We can also assume there is millions of files where hackers can easily add their
malicious code as it was done with SolarWinds and department of defense case. We do
not want the IT community to forget that hackers have the actual vendors' code, can
use reverse engineering to figure out the code structure and methods and hackers can
also add their malicious code to any of the vendors files.
Anyone can raise These questions:
• Are these vendors paying hackers to keep them from attacking their clients?
• Do we have a bulletproof Cybersecurity?
Our Answer:
Invest in building homegrown system where the only risk is the resource and time used
building these homegrown system. Virtual testing would the proof of how secure such system.
We have architected-designed the following to replace these vendors' tools and secure any system:
• Data, Database Replacement and the End of Database
• Virtual Container and Components
• Virtual Integration
• Behind the Scene Machine Learning and the Future of Machine Learning
• DevOps and DataOps
• Big Data and CRM
• Cybersecurity
• Automating Cybersecurity Detection - Adam's Blueprint for Security
• Reverse Engineering
• Virtual Testing
• Management
• Vertical Scaling of Data Centers
See our Object Oriented Cybersecurity Detection Architecture (OOCDA) Suite:
Object Oriented Cybersecurity Detection Architecture (OOCDA) Suite
Vendors' Software
|
1.
|
AWS: web hosting services
|
|
2.
|
Ansible: software provisioning, configuration management, and application-deployment tool enabling infrastructure as code.
|
|
3.
|
Bamboo: a continuous integration (CI) server that can be used to automate the release management for a software application, creating a continuous delivery pipeline.
|
|
4.
|
Bitbucket: Git - code repository management
|
|
5.
|
Chef: cloud configuration management and deployment application
|
|
6.
|
Codeship: cloud-based application development platform that helps businesses with continuous integration and deployment of applications
|
|
7.
|
Confluence: help teams to collaborate and share knowledge efficiently. With confluence, we can capture project requirements, assign tasks to specific users, and manage several calendars at once with the help of Team Calendars add-on.
|
|
8.
|
DataDog: monitoring and analytics tool for information technology (IT) and DevOps teams that can be used to determine performance metrics as well as event monitoring for infrastructure and cloud services. The software can monitor services such as servers, databases and tools.
|
|
9.
|
DC/OS: DC/OS stands for Data Center Operating System
|
|
10.
|
Docker: a set of platform as a service products that use OS-level virtualization to deliver software in packages called containers
|
|
11.
|
Elasticsearch: search and analytics engine. It allows you to store, search, and analyze big volumes of data quickly and in near real time.
|
|
12.
|
Git: Git is a version control system to manage source code history
|
|
13.
|
GitHub: a hosting service for Git repositories
|
|
14.
|
Kafka: Distributed, durable, fault tolerant, high throughput pub-sub messaging system
|
|
15.
|
kanban: Framework used to implement agile and DevOps software development
|
|
16.
|
Kubernetes: container orchestration (coordinating) system for automating software deployment, scaling, and management.
|
|
17.
|
Jenkins: continuous integration/continuous delivery and deployment (CI/CD) automation software DevOps tool written in the Java programming language. It is used to implement CI/CD workflows, called pipelines.
|
|
18.
|
JIRA: a proprietary issue tracking product - allows bug tracking and agile project management
|
|
19.
|
JUnit: a unit testing framework for the Java programming language
|
|
20.
|
Maven: Tool which build an manage java based code
|
|
21.
|
Nagios: software application that monitors systems, networks and infrastructure. Nagios offers monitoring and alerting services for servers, switches, applications and services.
|
|
22.
|
NGINX: a web server that can also be used as a reverse proxy, load balancer, mail proxy and HTTP cache
|
|
23.
|
NSQ: a realtime distributed messaging platform designed to operate at scale, handling billions of messages per day. It promotes distributed and decentralized topologies without single points of failure, enabling fault tolerance and high availability coupled with a reliable message delivery guarantee
|
|
24.
|
Puppet Lab: systems management tool for centralizing and automating configuration management. The Puppet Labs website offers a number of community modules for describing and managing infrastructure as code.
|
|
25.
|
Redis: is an in-memory data structure store, used as a distributed, in-memory key–value database, cache and message broker, with optional durability. Redis supports different kinds of abstract data structures, such as strings, lists, maps, sets, sorted sets, HyperLogLogs, bitmaps, streams, and spatial indices
|
|
26.
|
RKT: an application container engine developed for modern production cloud-native environments
|
|
27.
|
Splunk: is used for monitoring and searching through big data. It indexes and correlates information in a container that makes it searchable, and makes it possible to generate alerts, reports and visualizations
|
|
28.
|
Se (Selenium): tool that automates web browsers. It provides a single interface that lets you write test scripts in programming languages like Ruby, Java, NodeJS, PHP, Perl, Python, and C#, among others.
|
|
29.
|
SBT: build tool for Scala and Java projects, similar to Apache's Maven and Ant. Its main features are: Native support for compiling Scala code and integrating with many Scala test
|
|
30.
|
Terraform: an infrastructure as code (IaC) tool that allows you to build, change, and version infrastructure safely and efficiently. This includes low-level components such as compute instances, storage, and networking, as well as high-level components such as DNS entries, SaaS features, etc.
|
|
31.
|
Ubunto: an open-source and freely available operating system, one of the Linux distributions.
|
|
32.
|
Wave: Wave is a company that provides financial services and software for small businesses
|
|
33.
|
Zookeeper: server which enables highly reliable distributed coordination. ZooKeeper is a centralized service for maintaining configuration information, naming, providing distributed synchronization, and providing group services.
|
|
|


