
Sam Eldin |
CV - Resume | Tools 4 Sharing | Architects 2 Show | Big Data Presentation | Android Training | Java-Unix Code Templates | Interviews QA & Code |
|---|
|
|---|
|
Object Oriented Cybersecurity Detection (OOCD)©
Main Issues: Our main challenge(s) in this page is how can we unit and bring everyone involved with Cybersecurity and the future of Cyberspace to think in new ways outside their confront-zone. Cybersecurity experts are on the defensive and not willing to look further than what they know and conformable with. There is a lot of uncertainties and regardless of the company's size, the risks are high. They depend solely upon Cybersecurity vendors to solve their problems. Object Oriented Design and methodologies are not a new concept nor is a rocket science. We believe our Cybersecurity experts need to take the advantage of such simple OOD and its powerful tools proven by development community. This page covers: • Malware and Our Object Oriented Cybersecurity Detection (OOCD) • Our OCCD - What, How and Who • Our Virtual Detection Container and Components • Technical Details Malware and Our Object Oriented Cybersecurity Detection (OOCD): Let us list the names of the malware which we know so far: Phishing, Spear Phishing, Pharming, Malware, Cross-site scripting (XSS), Ransom-ware, Spoofing, Malvertising, Rogue Security Software, Drive-by, Drive-by-Downloads Attack, Distributed Denial of Service, Botnets, Smurf, TCP SYN Flood, Teardrop, Ping of Death, Man in the Middle, Session Hijacking, IP spoofing, Replay, Eavesdropping, AI-Powered, Password Attacks, Brute force, Phishing internal, Business Email Compromise, Ransomware, Spyware, Viruses, Macro Viruses, Trojan, Worms, Root Kit, Remote Access, Blended Threat, SQL Injection, DNS Tunneling, Crypto mining Malware, Crypto jacking, Zero-Day Exploit, Birthday Attack, Wiper Insider Attacks, Advanced Persistent Threats, Data Breach, Data poisoning, OS Command Injection, Application Vulnerabilities - Exploit Kit, OS Trap Door, Logic Bomb, Stack and Buffer Overflow, Viruses, Password assault, Denial of Service, Code Execution, Running Unnecessary Services, Memory Corruption, Non-updated Hypervisor, Wiper Malware, ..etc. We listed over 60 name and each one of them has its own unique characteristics plus may share other characteristics with other malware. Our thinking on how to detect each one or all of them may require that we should be thinking in Object Oriented Design (OOD) plus we need to think in what we call: Object Oriented Cybersecurity Detection (OOCD) What is Object Oriented Design (OOD)? OOD is the thinking and the creating of an object which would solve problems. OOD main objective is reusability. Our job here is not to teach OOD, but use OOD to solving our Cybersecurity detection issues and cash-in on the object's reusability. In OOD thinking, an object has: • Properties • Methods • Can be inherited - reused In OOD thinking, there is must be a Parent Object or Base Object which other object can inherit or reuse. OOD helps in setting standards and standardize methodology and approaches. For example, Java is a programming language and a development tool which is a world standard. Java also has an ocean of programming methods and objects (available to be reused) which help in developing almost any application (cloud, security, desktop, mobile, tablets, ..etc). Java should be our model to follow and learn from to make our OOCD goals and tasks achievable. Our OCCD - What, How and Who? Our attempt is to present the following: • What is Object Oriented Cybersecurity Detection (OOCD)? • Our short term goal • Our long term goal • OOCD Structure • What is the main job of our OOCD? What is Object Oriented Cybersecurity Detection (OOCD)? OOCD is an object which performs Cybersecurity detection. Therefore, we need to think and create OOCD object. Cybersecurity detection is not a simple task nor has one answer, but structuring detection into an object with tools and methods is the perfect base to build on. Our Short Term Goal: Our short term goal is building the basis for OOCD and set the structure for our new approach to Cybersecurity, Our Long Term Goal: Unit the Cybersecurity community and build a united front in the cyber ware. We need to build standards similar to Java and the Java community. OOCD Structure: The main objective is to build the basis which can be used as a foundation for further building, advancement and addressing complexities. Our task is not simple, but we need to divide our tasks into smaller manageable-reusable-inheritable steps. Container and Components: We call each Independent Virtual Sever a "Container", since it has its own operation system (OS) and all the supporting system software to run as a cloud virtual server. A "Component" is an application or a cloud application which runs within a Container. One Container may have one or more Components running within this container. 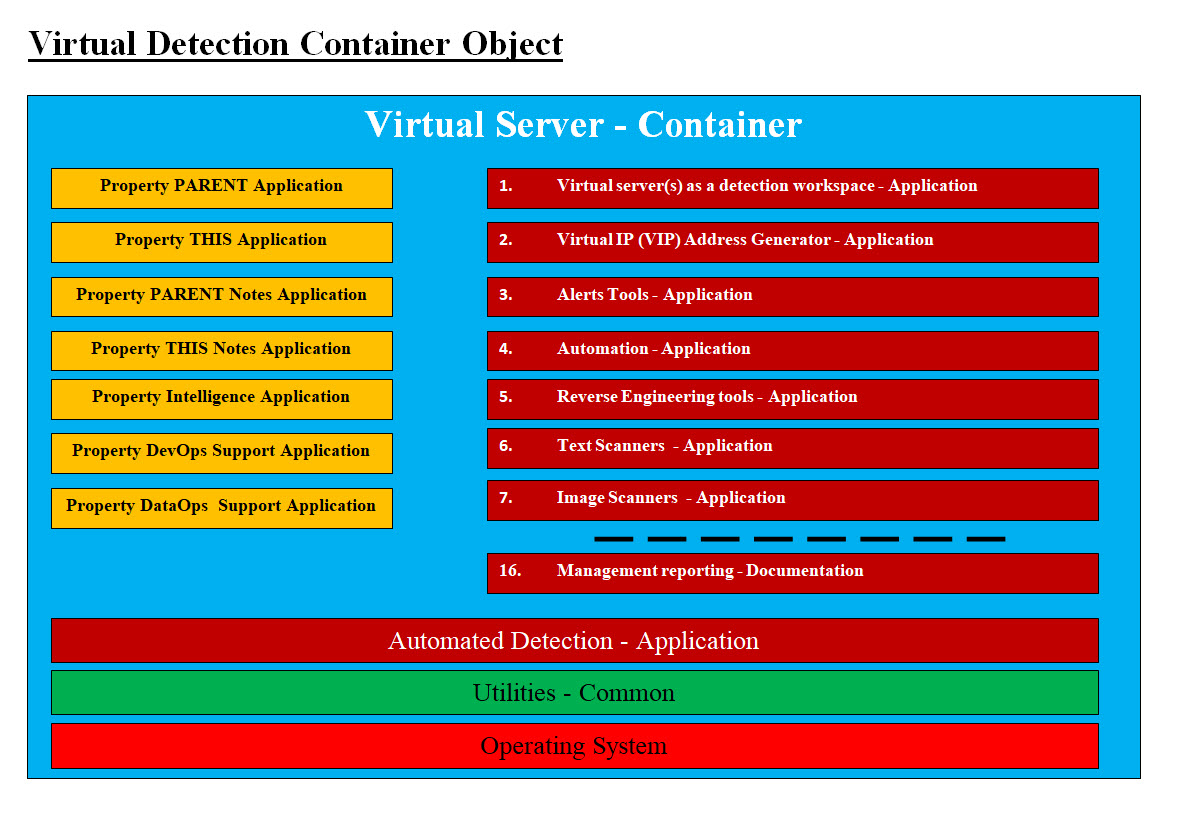
Image #1 Image #1 represents our Virtual Detection Container Object. It has a number of applications as components. We created separate applications-components which perform our OOCD Properties tasks. We also have another set of applications-components which performs the Methods applications. Utilities and Common are a set of applications which supports all the OOCD components. Automated Detection - Application is the automated engine which runs the virtual container's services. The Operating System (OS) runs all the applications within this container. Syntax: The following is our first OOCD syntax and we would be adding more as we get deeper into building the basic structure. • BASE = the starting object and the parent of all objects - has no parent - NULL • PARENT = Parent object or the starting BASE Object • THIS = the current object or the working object which is running the detection OCCD Properties: Properties are running applications which handle data and documentation in any format. First, Properties as running applications would free Cybersecurity staff-worker from knowing OOCD data, data complexities and data handling. All the Cybersecurity staff, he/she needs is to run the Properties application to handle the data processes without any further action or comprehension of what is running behind the scene. For example, Cybersecurity staff do not need to know Integer data type or any programming data type. A staff only needs to run the Properties application. For example, PARENT application has a feature of proving a list of all the malicious IP addresses. The staff would run PARENT Properties application to check if an IP address is in the PARENT malicious IP address list. We are not doing the firewalls' job, but we are adding dynamic updates to our handling of malicious requests. Therefore a newly encounter malicious IP address would be added to OOCD object. The OOCD object and all its children objects would know about this new malicious IP address without checking with any firewall. The following Properties have the data required by the running OCCD Methods and communication: 1. PARENT - what is being inherited from the parent which may not be the BASE object 2. THIS - OOCD IDs and data for tracking, permission and access 3. PARENT notes 4. THIS notes 5. Intelligence - has the matrices for using Numbers, Formulas and Algorithms 6. DevOps support 7. DataOps support Note: We may rename both Properties applications and Methods applications since we are in the early stage of OCCD building. OCCD Methods: Methods are executable programs and scripts which perform detection services: 1. Virtual Server(s) as a detection workspace 2. Virtual IP (VIP) Address Generator 3. Alerts tools 4. Automation 5. Reverse Engineering tools 6. Text Scanners 7. Image Scanners 8. ".exe" file Scanners 9. Memory Scanners 10. Operating System trapping 11. Machine Learning (ML) Tools 12. Terminating Processes and Application tools 13. Remover-kill-deletion-cleansing utilities 14. Testing 15. Reporting - teams, clients, staff, ..etc 16. Management reporting - Documentation Note: The functionalities of each of OOCD Methods would be covered in the detailed section. Anyone would be able to add properties and methods as needed. The added properties and methods would be only known to THIS object and any object which would inherited it. Automated Detection Application: This is an automated application which can be executed manually or scheduled. Utilities and Common: Utility and Common software are software programs which provide improved functionality plus reduce redundancies. In our detection object Utilities and Common are the supportive tools to Properties and Methods applications. Light Weight OCCD Object: Detection's performance in any cloud is critical plus any bare-metal memory size has limited capacity in the creation of our Virtual OOCD object (virtual server). The two main factors are size of OOCD Container (virtual server) and speed of its automated creation. We architected what we call Light Weight OOCD Container as shown in Image #2. It has the bare-bone structure and functionalities to perform speedy detection. 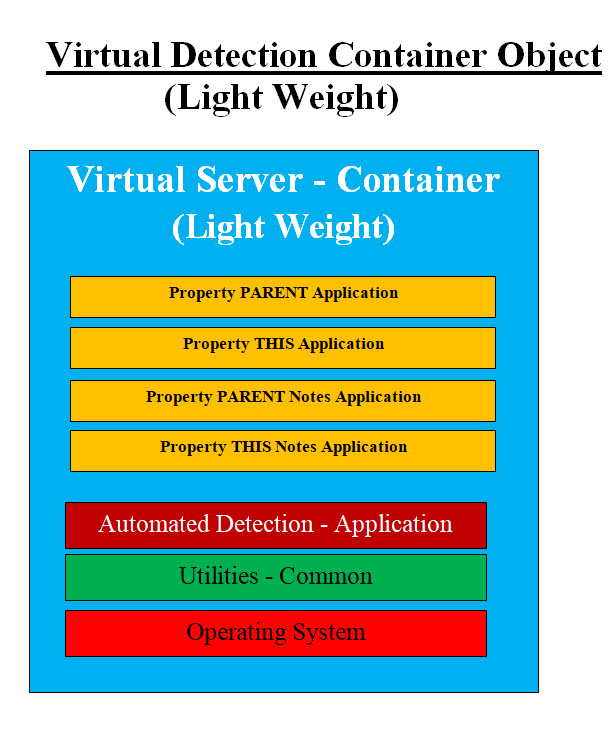
Image #2 For example, in September 09,2021, the Russian tech giant Yandex was hit with the biggest DDoS Attack ever. The flood of junk traffic, meant to overwhelm systems and take them down, peaked on September 5, but Yandex successfully defended against even that largest barrage. The company said in a statement. • “Our experts did manage to repel a record attack of nearly 22 million requests per second,” • “This is the biggest known attack in the history of the internet.” • 22 million requests per second Most servers usually can take around 256 or fewer requests per second. You can push it up to 2000-5000 for ping requests or to 500-1000 for lightweight requests. Our answer to such attack is the creating of our Light Weight OOCD object. With its small size and the ability to track malicious IP address dynamically plus terminate the malicious connection. Development Language: The development of the OOCD object can be implemented in Java, Python, C, C++ plus Linux, Unix and Windows scripts. Who would be using OOCD? There will be the following options: 1. Manual, where a Cybersecurity professional would be able to create OOCD object and run it 2. An automated and scheduled OOCD object(s) would be running as scheduled 3. A combination of option #1 and #2 How to use OOCD? Based on the type of suspected malware, a virtual server (THIS) would be created with all the OOCD properties ready to use including the automation detection part. The starting of the obejct creation can be done manually or automated. Our Virtual Detection Container and Components 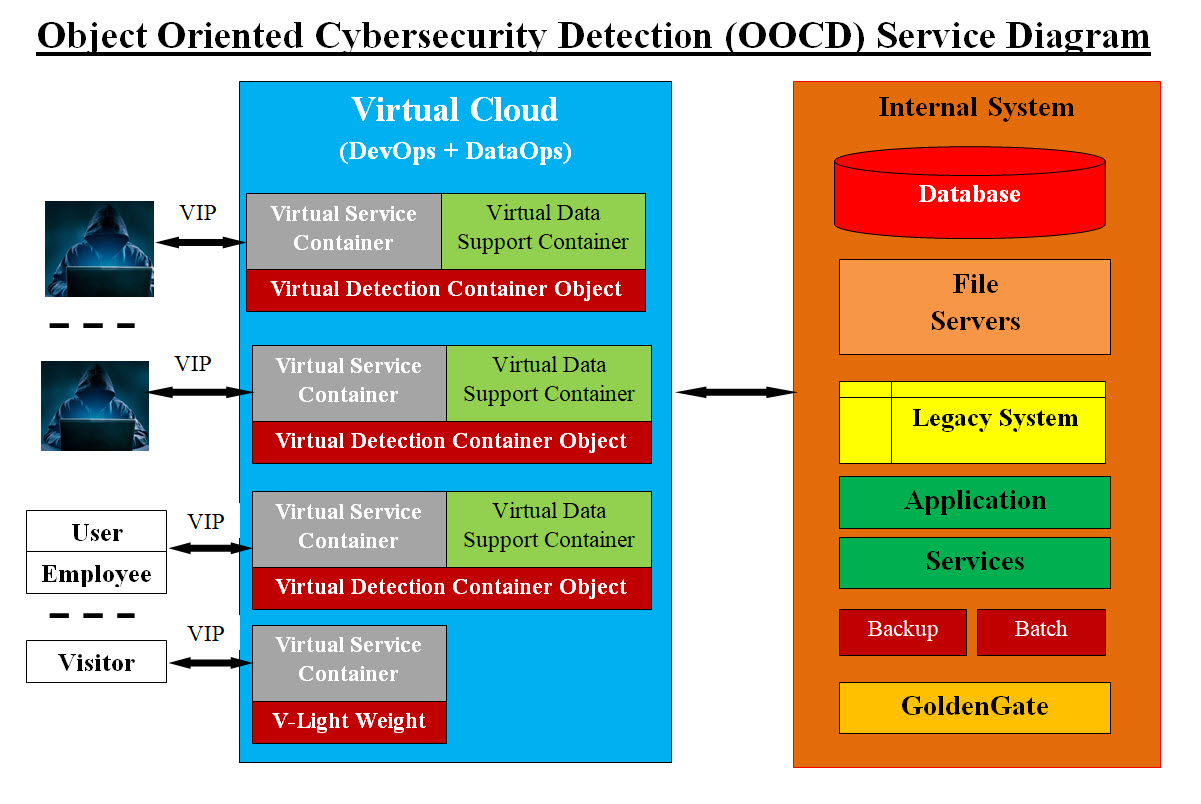
Image #3 Image #3 represents our Virtual Detection Buffer as a Virtual Cloud. It has Virtual Containers and Components are created dynamic and terminate within the Virtual Cloud and shielding the internal system. Our OOCD objects create the virtual service container object and data support container object. Virtual IP (VIP) addresses are generated and would not be reused. Hackers would not be able to use VIP for further attacks. Our OOCD object would would still mentor these object regardless if the users are clients, employees, visitors or even hacker with stolen credentials. These hackers would not pass our Virtual Cloud Buffer. Our virtual service container object and data support container object are presented in the following sections. Virtual IP (VIP) Address: For every virtual object (virtual server), our OOCD Method "Virtual IP (VIP) Address Generator" would create a VIP address to connect to the object. The only way to get to such virtual object is by using the supplied VIP address. These VIP addresses are dynamic and created on the fly by Method "Virtual IP (VIP) Address Generator". Once the requested task is done, such VIP address would not be used again for as long as we can see that its save to reuse it. What is the main job of our OOCD? The main job of our OOCD is detection and prevention of malware attacks. In short, our OOCD is the gate guard which intercepts, detects, prevents and eliminates any malware attacks. To help in the protection of system services and data, we also creating the following: • Virtual Service Container Object • Virtual Data Support Container Object DevOps and DataOps are the main support for creating these containers. Virtual Service Container Object: Our Virtual Service Container Object is nothing more than a virtual server as a container which has the requested services by a client, visitor, partner, employee, or even a hacker, ..etc. It has its own OS and runs only one application with the application supportive software or services. Once the requested service is done executed, the entire virtual service container and its components are wiped clean out the memory and the system. 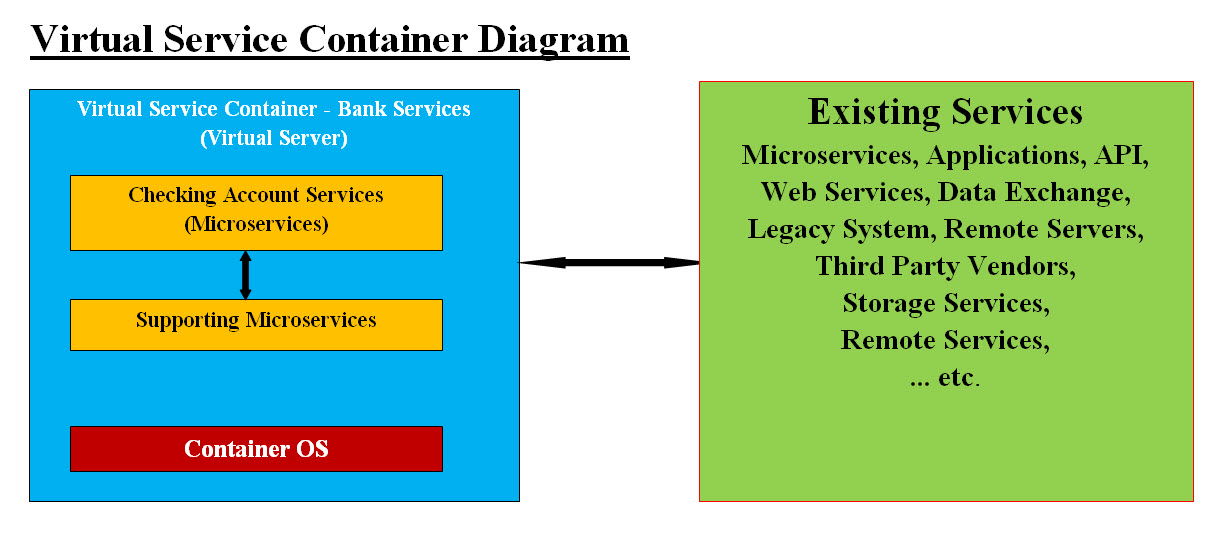
Image #4 Image #4 represents our Virtual Service Container (virtual server) with its Operation System (OS). It is created to handle a cloud request for a specific service. Our OOCD object Method Virtual Server(s) Application would create this Virtual Service Container (virtual server). Our OOCD object's Method Virtual IP (VIP) Address Generator will generate a Virtual IP address (VIP) referencing-pointing to Virtual Service Container. Virtual Data Support Container: 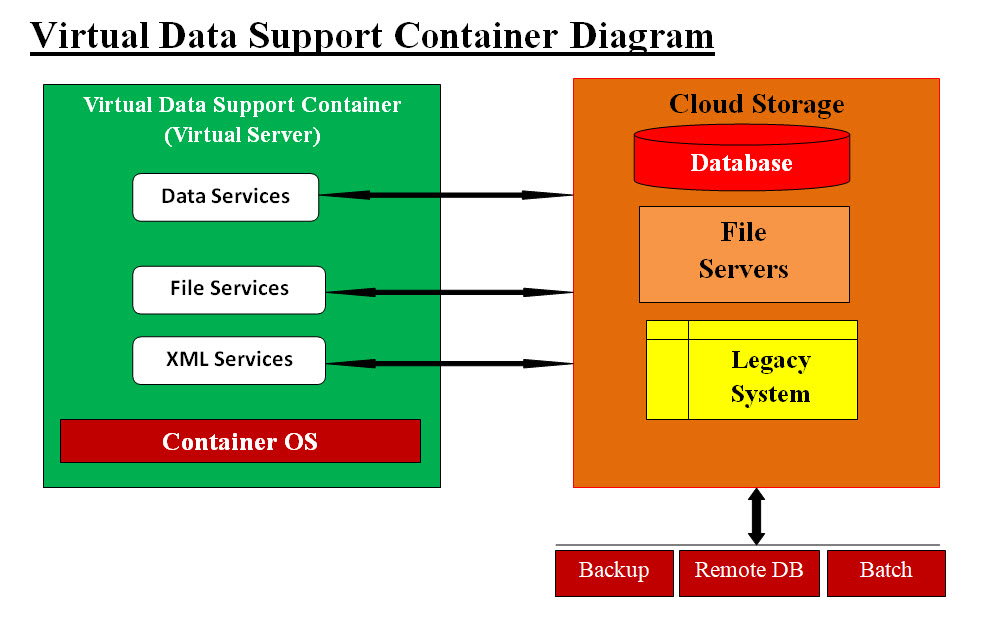
Image #5 Image #5 represents our Virtual Data Support Container object. It is created by our OOCD object Method Virtual Server(s) Application. It is the Virtual Data Support Container (virtual server) object. Our OOCD object's Method Virtual IP (VIP) Address Generator will generate a Virtual IP address (VIP) referencing-pointing to it. Technical Details Let us examine each of OOCD Properties: - Coming Soon PARENT - what is being inherited from the parent which may not be the BASE object THIS - ID for tracking, permission and access PARENT notes THIS notes Intelligence - uses matrices for using Numbers, Formulas and Algorithms DevOps support DataOps support Let us examine each of OOCD Methods: OCCD Methods: - Coming Soon Methods are executable programs and scripts which perform detection services: 1. Virtual server(s) as a detection workspace 2. Virtual IP (VIP) Address Generator 3. Alerts tools 4. Automation 5. Reverse Engineering tools 6. Text Scanners 7. Image Scanners 8. ".exe" file Scanners 9. Memory Scanners 10. Operating System trapping 11. Machine Learning (ML) Tools 12. Terminating processes and application tools 13. Remover-kill-deletion-cleansing utilities 14. Testing 15. Reporting - teams, clients, staff, ..etc 16. Management reporting - Documentation |
|---|