
Sam Eldin |
CV - Resume | Tools 4 Sharing | Architects 2 Show | Big Data Presentation | Android Training | Java-Unix Code Templates | Interviews QA & Code |
|---|
|
|---|
|
Security - The Next Generation
Cyber Security is still a hot topic and it is a never ending battle. We believe we have answers to Security and our attempt here is to present our Cyber Security Solution(s). Introduction: It is very important is create a picture of what we are dealing with. Such picture or image would help all the parties involved to be on the same page and eliminate any misunderstanding or ambiguity. It also puts a clear cut of the final goals. Image #1 is a rough draft of a cloud services, its major components, the protection layers and the 24X7 attacks on it. So far the protection layer(s) (HTTPS, Firewalls, Server Security, Sockets, Security (SSL), Encryption-Decryption, Authentication, Authorization, Application Security, Third party Security, Other Security, Database Security) did not succeed in stopping attacks, nor protected the cloud services. The Internal Hacking or Insider threats is the major issue which must be addressed by any security system. 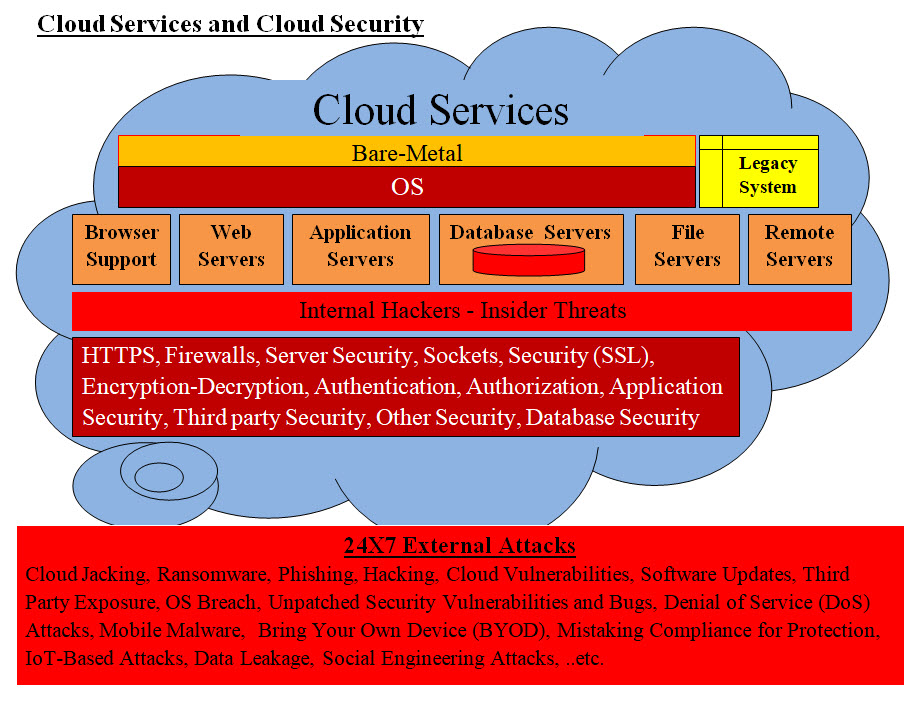
Image #1 Our Security Approach: Our approach is summarized as follows: • First we must have a strategy(s) • Provide Options or choices • Architect a number of possible solutions • Brainstorm these possible solutions on how to economically develop, test, implement and maintain them Our Strategies: To help our strategies we need to think in a number of terms. First, how hackers and specially internal hackers think and operate. What tools they use and how do they find vulnerabilities in their target system. We also would not be able to close all the system holes and gaps, but we can use the strategy of keep the target moving (created and deleted) so any hacker attempt would have to start all over again. The question is how economically and easily can we implement these strategies plus do the training and maintaining of these implementations. The following are a list of strategies: 1. Virtual Proxies, Virtual Servers, Virtual IP Addresses and Virtual Objects 2. The use of Machine Learning to provide guidelines of protecting the cloud services 3. Closed Box Virtual Database Services 4. Chip to Chip Communication 5. Dynamic Virtual redundancies of Virtual cloud services 6. Use of NAS as backup and rollback storage 7. Using logging, tracking and audit trial - internal hackers 8. Training employees and cloud services users on protecting against hackers 9. Brainstorm the development cost and performance of our architected solutions Quick overview of the Implementation of Our Strategy: Virtual Proxies, Virtual Servers, Virtual IP Addresses and Virtual Objects We need examine the following facts:
Using virtuality to create queues of virtual service objects and its virtual IP address. The routers would be routing front objects in the queues with their virtual IP address, while the old ones are released and their memory space is released for reuse. This needs to be well developed, implemented and tested before they are used. It also have to be practical. The great thing is that virtual objects can be created and released with hardly any effort. We are hoping creating such a short terms services, processes or objects, where hackers attacks would be terminated. The use of NAS can come handy to help with saving and rollback processes with very low cost. NAS would be used to store Java Data Access Objects (DAO) with a timestamp. The use of Machine Learning to provide guidelines of protecting the cloud services: HTTP requests have an abundant amount of data which our Machine Learning code would be looking for patterns, sources, servers, countries, regions, users, .. etc to create lists for our firewall to block and prevent accesses and possible attacks. Also Machine Learning would looking at our services objects, exceptions, errors, logging and tracking and look for issues, performance, vulnerabilities and handlings. Closed Box Virtual Database Services: The goal is to provide no access to database or filing system except through an interface with parsers. Any database or files requested is parsed and then performed by the interface code and then returns the result. An unauthorized or illegal request is flagged and stopped. Audit trail, logging and tracking are used and copies are sent to Machine Learning services to help figure out any hacking attempts, patterns and frequencies. The Machine Learning services would provide guidelines for system security. Chip to Chip Communication: See the following link: http://gdprarchitects.com/CompressionEncryptionPage.html Dynamic Virtual Redundancies of Virtual Cloud Services: See virtual page: http://sameldin.com/SamQualificationPages/Virtualization.html Use of NAS as Backup and Rollback Storage: NAS would be used to store Java Data Access Objects (DAO) with a timestamp. Backup and rollback processes and their mechanisms must be faultless and fast. Possible buffers (linked List objects) would be used to speed the saving and rollbacks since they are running in memory. Using Logging, Tracking and Audit Trial - Internal Hacker Tracking system performance, issues, leaks, vulnerabilities. Audit trial would help track users and access of system resources. Training Employees and Cloud Services Users on Protecting Against Hackers Employees and users are the human factor in protecting our cloud services. They must be trained to help protect our services. Processes, procedures, training, protocols, handlings and documentation are needed to insure no human errors take place. Brainstorm the Development Cost and Performance of Our Architected Solutions: There is a big difference between fanatic and reality. An architect-tech lead-tech manager must answer the following questions: • Is the development of the target system doable? • What are the cost of developing such system in term cost, time and effort? • What are the "have-to-Have" and "Nice-to-Have"? • How to get our team ready to develop such system within budget and on time? As a team player, I will need to brainstorm these questions with my team and listen to my team's thoughts, suggestions, comments, questions and concerns. |
|---|